What is the Caesar cipher? Definition, history, and examples

Over 2,000 years ago, Julius Caesar had his own way of keeping sensitive messages out of enemy hands. This ancient code, known as the Caesar cipher or Caesar encryption, is one of the earliest known encryption techniques. While far too simple to stand up to modern security standards, it remains a fascinating relic of how secret communication began and a reminder that the need to protect information is as old as history itself.
What does the Caesar cipher mean?
The Caesar cipher is one of the oldest known cryptographic methods, named after Julius Caesar, who reportedly used it to keep his military messages secret. It works by systematically replacing each letter in a message with another letter a fixed number of positions away in the alphabet, a simple but clever way to keep intercepted orders useless without the right key.
Back in ancient times, communication relied on couriers, messenger pigeons, and other physical methods, none of which were particularly secure. If a message was captured, the enemy could read it. By using the Caesar cipher, even if a scroll fell into the wrong hands, its contents would remain meaningless unless the reader knew the key.
While modern computers can break it in seconds, this method remains a fascinating example of how humans began protecting information. Its historical significance also ties into the broader history of encryption.
How the Caesar cipher works
The Caesar cipher uses a fixed shift value (called the key) to transform each letter. For example, with a shift of three (n = 3), A becomes D, B becomes E, and so on, looping back to A after Z.
| Alphabet | n = 1 | n = 3 |
| A | B | D |
| B | C | E |
| C | D | F |
| D | E | G |
| E | F | H |
For example, with n = 1, BED becomes CFE, and with n = 3, BED becomes EHG.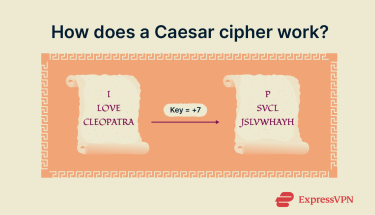
Try it yourself
You can easily recreate this ancient cryptographic method yourself:
- Write the alphabet from A to Z.
- Choose a shift value (key) between 1 and 25.
- Shift each letter forward by that amount, wrapping from Z back to A.
- Replace each letter in your plaintext with its shifted version.
Use online Caesar cipher tools
If you’d rather skip the manual work, there are plenty of online tools that can encrypt and decrypt Caesar cipher messages instantly. For example, cryptii’s Caesar cipher tool lets you paste in text, choose your shift value, and see the result immediately.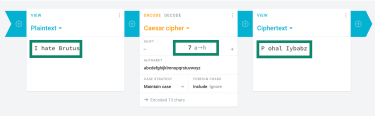 These tools are great for experimenting with different keys, checking your manual work, or quickly encoding short messages for fun or educational purposes.
These tools are great for experimenting with different keys, checking your manual work, or quickly encoding short messages for fun or educational purposes.
Strengths and weaknesses of the Caesar cipher
The Caesar cipher might be ancient, but it still has its perks and plenty of downsides. It’s simple enough to scribble out on a scrap of paper, yet easy enough for a curious mind (or modern computer) to crack wide open. Let’s break down where it shines and where it falls flat.
Advantages of the Caesar Cipher
When it comes to simplicity and accessibility, this cipher definitely has a few things going for it:
- Easy to implement: You don’t need advanced tools or complicated mathematics to put it into practice. A pencil, paper, and knowledge of the shift value are all you need.
- Simple pre-shared key: As long as the sender and recipient agree on the shift value beforehand, the encrypted message can be quickly decrypted without any additional instructions.
- Easily adjustable: The shift value can be changed at any time, and variations (such as shifting only certain sections of a message) can be introduced for a little extra obscurity. The only requirement is that the new key must be shared securely with the recipient.
- Great for beginners: The Caesar cipher is an approachable way to learn the basics of encryption, substitution ciphers, and the concept of keys. It serves as a stepping stone to understanding modern encryption methods.
Limitations and vulnerabilities
Unfortunately, its simplicity is also its downfall. Here’s where the Caesar cipher falls short:
- Low security: To a determined interceptor, the Caesar cipher poses very little challenge. Even without computer assistance, a skilled cryptanalyst could crack it by looking at letter frequencies and patterns.
- Limited keyspace: With the English alphabet, there are only 25 possible shifts. That’s small enough for someone to try every possibility manually in minutes or instantly with a computer.
- Lack of confidentiality safeguards: The cipher offers no way to detect if a message was intercepted or altered during transmission. Anyone who guesses or discovers the key can read the entire message.
Why it's no longer used for secure communication
The Caesar cipher’s main problem is that it’s just too easy to break. In a world where data isn’t limited to short notes but includes massive text files, images, videos, and other formats, this kind of encoding doesn’t stand a chance. Besides, manually shifting letters in a 1,000-word document would be painfully slow and still crackable in seconds by even the simplest modern decryption tools.
It also preserves the length and structure of the original message, which gives attackers extra clues. For example, “BED” becomes “CFE” with a +1 shift, which is still three letters long. Compare that to AES encryption, where “BED” encoded with the “CaesarCodeRocks!” key might look like “Wvg/+IUIZ/xLrXgahSTUeg==”.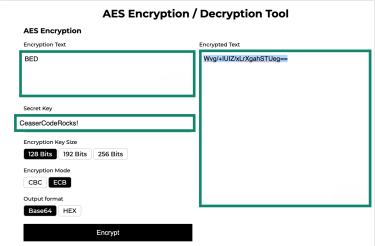 We generated this AES example using Anycript, an online tool that makes it easy to try out different encryption and encoding methods side by side. As you can see, modern encryption hides the original length, scrambles the structure, and makes brute-force attacks far less effective. That’s why the Caesar cipher is now more of a teaching tool than a serious way to protect sensitive information.
We generated this AES example using Anycript, an online tool that makes it easy to try out different encryption and encoding methods side by side. As you can see, modern encryption hides the original length, scrambles the structure, and makes brute-force attacks far less effective. That’s why the Caesar cipher is now more of a teaching tool than a serious way to protect sensitive information.
Learn more: If you want to explore more ways to keep your data secure, check out what a hacker can teach you about keeping your systems safe.
Caesar cipher in modern security and education
While the Caesar cipher isn’t anywhere near robust enough for modern cryptography standards, it still has its place.
Use in puzzles and classrooms
Today, the Caesar cipher shows up in everything from escape room challenges to puzzle books, where it offers a simple but fun way to apply basic encryption.
In classrooms, it’s a great tool for introducing students to cryptographic thinking because it contains all the core building blocks (key, plaintext, and encrypted text) that modern algorithms also use.
Legacy in cybersecurity
While it’s obsolete for secure communication, the Caesar cipher still has a place in cybersecurity culture. It’s a popular teaching tool in Capture the Flag (CTF) competitions, cybersecurity awareness events, and beginner coding challenges.
It’s also a reminder that what’s secure today might be vulnerable tomorrow, making constant encryption evolution essential for keeping data safe in the future.
Relevance to online privacy
Like many modern algorithms, the Caesar cipher uses symmetric encryption, where the same key is used for both encryption and decryption. Today, advanced symmetric algorithms like AES protect everything from government communications to the data stored by tech giants like Apple and Google.
Top-tier VPNs, such as ExpressVPN, also rely on strong encryption to create secure tunnels between your device and their servers, shielding your activity from prying eyes.
Comparison to other encryption methods
Not all encryption works the same way, and the Caesar cipher is about as basic as it gets. To see where it stands, let’s compare it to other common methods.
Substitution vs. transposition
The Caesar cipher is a substitution cipher. That means each letter in the message is replaced with another, based on a fixed rule, like shifting every letter three places forward in the alphabet. Transposition ciphers, on the other hand, keep the letters the same but shuffle their order.
For example, if our plaintext is BEAD:
- Substitution (shift of 3): EHDG
- Transposition: ABED
Transposition ciphers are considered stronger than substitution ciphers because they’re less vulnerable to frequency analysis. They can also be made more challenging by altering character groupings, such as transposing LIGHTWAY PROTOCOL into WILT CLOG HARP OTOY. Still, even these are easy pickings for today’s computers.
Caesar vs. AES and RSA
Today, a Caesar cipher decoder can crack a message in less than a second, even on your phone. That’s a massive leap from the days when this cipher was trusted to secure military orders.
By contrast, modern encryption methods like Advanced Encryption Standard (AES) and Rivest–Shamir–Adleman (RSA) are on an entirely different level. It would take the most powerful supercomputer in the world trillions of years to even try all the possible combinations for a strong AES or RSA key.
However, even these aren’t bulletproof, especially with the looming threat of quantum computers. That’s why researchers are working on post-quantum cryptography: encryption methods designed to withstand the immense processing power quantum computing will bring.
FAQ: Common questions about the Caesar cipher
Is the Caesar cipher still used today?
The Caesar cipher is still used today in games, puzzles, and cybersecurity education. It’s a common feature in Capture the Flag competitions, beginner coding challenges, and classroom exercises that introduce students to basic cryptographic concepts.
Can the Caesar cipher be cracked easily?
The Caesar cipher can be cracked easily due to a small number of keys (such as 25 for the English alphabet) and the fact that each encrypted word retains the same characteristics (such as length) as its decrypted version.
What’s a real-world example of the Caesar cipher in use?
One modern example is ROT13, a simple Caesar cipher variant that shifts each letter in the alphabet 13 positions before substituting it. It’s been used on forums and newsgroups to hide spoilers, puzzle answers, or off-color jokes, making the text unreadable unless someone deliberately decodes it. ROT13 has even appeared in certain Windows XP registry keys, though purely for obfuscation rather than security.
Is the Caesar cipher symmetric or asymmetric?
The Caesar cipher is symmetric because the same key is used for both encryption and decryption. If you know the number of positions the letters were shifted to encrypt the message, you can simply shift them back by the same amount to decrypt it.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN