Port 443: What it is, how it works, and how to use it safely


Whenever you send sensitive information over the internet, such as credit card numbers, passwords, or personal details, Port 443 is the essential gateway that ensures your data reaches its destination securely. It serves as the backbone of HTTPS, encrypting your connection to protect it from prying eyes. From online banking to social media and e-commerce, Port 443 safeguards your digital activity by creating a secure pathway between your browser and the websites you visit.
But how exactly does Port 443 achieve such a high level of security? And why does it matter for everything from internet browsing to VPNs? This guide will demystify Port 443, explaining how it works, where it’s used, and how you can troubleshoot or secure it effectively. Whether you’re a casual internet user or a tech enthusiast, understanding Port 443 is key to navigating the internet safely and confidently.
Jump to…
- What is Port 443?
- How Does Port 443 Work?
- What is Port 443 Used For?
- Which Protocols Operate on Port 443?
- Is Port 443 Safe?
- How to Open Port 443 on Your Device
- Troubleshooting Port 443 Issues
- The Importance of Port 443 for VPNs
- Final Thoughts on Port 443
What is port 443?
Port 443 is the standard port for HTTPS, the secure version of HTTP. HTTPS is used by websites and other online services to protect your data from being intercepted by eavesdroppers. Imagine port 443 as a secure tunnel between your web browser and a website. When you visit a website that uses HTTPS, all communication between your browser and the website is encrypted through this tunnel. This means that even if someone were to intercept your traffic, they wouldn’t be able to read it.
What are ports?
A port is a virtual communication endpoint that is used by computers, servers, and networked devices to exchange data. It directs incoming and outgoing traffic to the appropriate programs or services, such as loading a webpage, sending an email, or accessing files remotely.
Ports play an important role in enabling multiple services to function simultaneously on a single device. They also help maintain security by allowing firewalls to block traffic on unused or unnecessary ports, protecting against unauthorized access.
Examples of common ports and their uses
Ports are an essential part of how devices communicate over a network. Each port serves a distinct purpose, from handling web traffic to ensuring secure connections for sensitive data.
Here are some of the most common ports and their typical uses, along with their benefits and potential drawbacks:
| Port number | Protocol/service | Common uses | Advantages | Disadvantages |
| 80 | HTTP | Loading websites with unencrypted web traffic. | Easy access for most websites; universally supported. | Traffic is vulnerable to interception or eavesdropping. |
| 443 | HTTPS | Secure web traffic, such as online banking and e-commerce. | Encrypts data; protects against interception and tampering. | Can still be exploited if SSL/TLS configurations are outdated. |
| 25 | SMTP | Sending emails. | Ensures email delivery across the web. | Vulnerable to spam and phishing attacks without proper security. |
| 22 | SSH | Secure remote access to servers. | Encrypts data; allows safe remote management. | Can be targeted by brute-force attacks if not secured. |
| 53 | DNS | Resolving domain names to IP addresses. | Essential for internet navigation. | Can be exploited in DNS spoofing attacks. |
Port 443 vs. Port 80: Key differences
When it comes to network ports and security, Port 443 and Port 80 are two of the most commonly used ports. They play essential roles in web traffic, but their functions and levels of security differ significantly. Here’s a closer look at the key differences between the two:
| Feature | Port 443 | Port 80 |
| Primary use | Handles secure web traffic via HTTPS, ensuring encrypted data transmission. | Used for unencrypted HTTP traffic, allowing general website browsing. |
| Security | Uses SSL/TLS encryption to protect data from interception or tampering. | Lacks encryption, leaving transmitted data vulnerable to eavesdropping and attacks. |
| Encryption | Employs 443 SSL to establish secure, private connections. | No encryption; all data is sent in plain text. |
| Applications | 443 protocol is vital for online banking, e-commerce, and any activity requiring data protection. | Suitable for non-sensitive applications or static website browsing. |
| Indicators | Websites using Port 443 display HTTPS in the address bar and a padlock icon in most browsers. | Websites using Port 80 display HTTP without the padlock, indicating the connection isn’t secure. |
| Opening the port | Configuring firewalls for opening Port 443 allows secure HTTPS traffic but must be managed securely. | Opening Port 80 enables HTTP traffic but increases exposure to potential |
| Vulnerabilities | Fewer vulnerabilities due to encryption, but outdated SSL/TLS configurations can be exploited. | Susceptible to man-in-the-middle (MITM) attacks, data theft, and other security threats. |
| Network role | The standard HTTPS port for secure communication on the internet. | Primarily used for basic, non-secure web communication. |
| Best for | Transmitting sensitive data, such as passwords, credit card details, or personal information. | Non-sensitive content or internal systems where security isn’t a concern. |
Which should you use?
For any activity involving sensitive data or secure data transmission, Port 443 is the clear choice. The adoption of HTTPS over Port 443 has become the global standard for websites aiming to protect users' privacy and security. In contrast, Port 80 should only be used for non-critical purposes where encryption isn’t necessary.
Why is Port 443 the Standard for HTTPS?
Port 443 is the default port used for secure web traffic through HTTPS. It’s the foundation of secure online communication, ensuring that your data is encrypted and protected as it travels between your browser and the websites you visit. Here’s why Port 443 has become the standard for secure connections:
1. HTTPS and secure data transmission
When you visit a website with HTTPS in the URL, your connection is routed through Port 443. This port uses SSL/TLS encryption to secure the data being transmitted, ensuring that sensitive information, such as passwords, credit card details, and personal data, remains private and protected. This encryption prevents cybercriminals from intercepting or tampering with your traffic.
2. The role of SSL/TLS
The 443 protocol relies on SSL/TLS to establish a secure connection between your device and the server. During this process, a handshake occurs to authenticate the website and exchange encryption keys. This ensures all communication through TCP 443 is encrypted and trusted, making it essential for activities like online banking, e-commerce, and logging into secure accounts.
3. Why Port 443 is preferred over Port 80
Unlike Port 80, which handles unencrypted HTTP traffic, Port 443 provides a secure channel for browsing the web. Websites using Port 443 show a padlock icon in the browser address bar, giving users confidence in the site's security.

In contrast, traffic over Port 80 is vulnerable to interception and should be avoided for sensitive tasks.
4. A global standard for secure connections
Most modern websites rely on HTTPS for secure communication, and Port 443 is the backbone of this standard. It’s supported by all major browsers and networks, ensuring compatibility and security for users worldwide. Additionally, browsers now flag HTTP-only websites as insecure, further cementing the importance of HTTPS and Port 443.
5. Beyond basic browsing
Port 443 isn’t just used for web browsing. It’s also essential for services like:
- VPN connections using 443 HTTPS to bypass network restrictions.
- Secure API communication between applications.
- Protecting sensitive business data in cloud services.
How does Port 443 work?
Port 443 works by using cryptographic protocols like TLS (Transport Layer Security). These protocols establish an encrypted connection between your browser and the websites you visit, ensuring data remains private and protected from interception. Let’s break it down further:
The role of SSL/TLS in secure communication
SSL (Secure Sockets Layer) and its successor, TLS, are the technologies that make Port 443 a secure gateway for web traffic. They encrypt data transmitted between your device and a server, preventing unauthorized access or tampering.
Here’s how SSL/TLS enhances secure communication:
- Authentication: SSL/TLS verifies the website’s identity through a certificate issued by a trusted Certificate Authority (CA). This ensures that users are connecting to a legitimate website, not an imposter.
- Encryption: All data transmitted over Port 443 is encrypted, ensuring confidentiality. Even if intercepted, the data would be unreadable without the decryption keys.
- Integrity: SSL/TLS ensures that data isn’t altered during transmission. If tampered with, the connection is terminated.
This trifecta of security—authentication, encryption, and integrity—is why Port 443 is the foundation of HTTPS connections.
Simplified explanation of the TLS/SSL handshake
The TLS/SSL handshake is the process that takes place when your browser connects to a website through Port 443. It might sound complicated, but here’s a simplified version of how it works:
- Hello exchange: Your browser sends a "Client Hello" to the server, listing supported encryption methods. The server responds with a "Server Hello," selecting the strongest encryption available.
- Certificate validation: The server sends its SSL/TLS certificate, proving its identity. Your browser checks that the certificate is valid and issued by a trusted authority.
- Key exchange: Your browser and the server securely exchange encryption keys to establish a private connection.
- Secure session: With the keys in place, all data sent and received is encrypted, ensuring a secure browsing experience.
This handshake happens in milliseconds, seamlessly securing your connection without interrupting your browsing.
Real-life examples of Port 443 in action
Port 443 plays a vital role in many industries where secure communication is critical. Here are a few examples:
- Banking and finance: Online banking platforms use Port 443 to encrypt transaction details and protect user accounts from cyberattacks.
- E-commerce: Secure online shopping platforms rely on Port 443 to safeguard payment information and maintain customer trust.
- Healthcare: Patient portals and telehealth services use Port 443 to protect medical records and private consultations.
- VPN services: Many VPNs utilize Port 443 HTTPS to bypass network restrictions and ensure encrypted traffic.
These industries depend on Port 443 to meet stringent security standards and keep sensitive data safe.
What is Port 443 used for?
Port 443 is the foundation of secure web communication, but its use goes far beyond just browsing the internet. It’s essential for transmitting sensitive data and maintaining secure connections in various online activities. Here’s a closer look at its everyday applications and why it’s indispensable.
Everyday applications of Port 443
Port 443 is used wherever secure communication is needed. Here are some of its most common applications:
- Online banking and e-commerce: Protects sensitive financial data, like credit card details and banking credentials, during online transactions.
- Social media platforms: Encrypts your activity on platforms like Facebook, Instagram, and Twitter to safeguard personal information.
- Healthcare services: Ensures secure access to patient portals and protects sensitive health records.
- Cloud storage services: Secures file transfers and account data for platforms like Google Drive and Dropbox.
- Email services: Encrypts access to secure email services, ensuring private communication.
Essentially, if a website or service uses HTTPS, it’s relying on Port 443 to provide secure, encrypted web traffic.
How VPNs use Port 443 to bypass restrictions
VPNs rely on Port 443 as a key tool for evading network restrictions and censorship. By blending VPN traffic with normal HTTPS traffic, VPNs can bypass even the strictest firewalls and access-blocking measures. Here’s how it works:
Disguising VPN traffic as HTTPS
Many VPN providers route their encrypted traffic through TCP 443, the same port used by HTTPS websites. Since HTTPS traffic is encrypted and indistinguishable from VPN traffic on Port 443, firewalls and network administrators are unable to differentiate between the two. This allows VPN connections to pass through undetected, even on networks with strict monitoring.
Evading firewalls and DPI (Deep Packet Inspection)
In some restrictive environments, authorities or organizations use technologies like deep packet inspection to analyze and block non-HTTPS traffic. By using 443 HTTPS, VPNs ensure their data packets mimic regular web traffic, preventing these systems from blocking or flagging the connection.
Bypassing government censorship
In countries with heavy internet censorship, where social media, news outlets, or messaging apps are restricted, VPNs running on Port 443 enable users to maintain access. For example, a VPN using Port 443 can encrypt and route your connection to access blocked services like WhatsApp, Facebook, or international news websites.
Accessing blocked content on corporate or school networks
Even on smaller scales, such as in workplaces or schools where certain websites or services are blocked, VPNs leveraging 443 SSL traffic allow users to bypass restrictions while maintaining secure communication.
Read more: The internet is safer now—but a VPN is still essential protection
Why Port 443 is critical in restrictive countries
Port 443 is essential in environments with strict censorship and surveillance because it enables secure and private internet access while being difficult to block. Here’s why it plays such an important role:
1. Widespread use of HTTPS
Port 443 is the backbone of HTTPS, the secure version of HTTP used by the majority of websites for encrypted communication. Governments and organizations hesitate to block it entirely because doing so would disrupt access to essential services like banking, healthcare, and e-commerce, as well as widely used platforms like search engines and social media.
2. Encryption as a shield
Traffic over Port 443 is encrypted using SSL/TLS, which means the data is scrambled and unreadable to anyone trying to intercept it. This encryption prevents censorship systems like deep packet inspection (DPI) from analyzing the content or filtering it based on specific keywords or patterns.
3. A gateway for circumventing censorship
In restrictive countries, VPNs and other secure tools rely on Port 443 to bypass firewalls. Since VPN traffic over Port 443 is indistinguishable from regular HTTPS traffic, it blends in seamlessly with normal web activity. This makes it incredibly difficult for authorities to identify and block without causing collateral damage to legitimate internet usage.
4. Preserving privacy
In regions where surveillance is common, Port 443 ensures that online communication—whether it’s accessing an international news website, sending private messages, or managing sensitive transactions—remains protected from prying eyes. This encryption gives users the confidence to communicate freely and access information without fear of monitoring.
Which protocols operate on port 443?
Port 443 is not exclusive to HTTPS—it also supports other protocols that benefit from its secure, encrypted communication. These protocols rely on SSL/TLS encryption to protect data during transmission, making Port 443 versatile in various contexts beyond standard web traffic.
HTTPS: The primary protocol on port 443
HTTPS remains the primary protocol that uses Port 443. It encrypts communication between browsers and servers, ensuring privacy and security. However, the role of HTTPS extends beyond traditional browsing. It supports:
- Web applications: Tools like secure payment gateways or cloud platforms.
- APIs: Secure communication between applications and services.
- IoT devices: Ensures secure data transmission between connected devices.
Other protocols that benefit from Port 443
While HTTPS dominates Port 443, several other protocols also leverage it for secure data exchange:
- FTPS (File Transfer Protocol Secure): FTPS uses SSL/TLS encryption to protect file transfers, often over Port 443 when other ports (e.g., 21 or 990) are blocked. This ensures safe handling of sensitive data during uploads and downloads.
- WebSockets over TLS (WSS): Applications requiring real-time data, like live chat or collaborative tools, use WSS for secure WebSocket connections. Routing through Port 443 ensures these connections are encrypted and accessible, even on restricted networks.
- VPN traffic: Many VPNs, including Lightway, can operate over Port 443. This approach disguises VPN traffic as HTTPS traffic, bypassing firewalls or censorship that typically block other VPN protocols.
- SMTPS (Secure Mail Transfer Protocol): SMTP, used for sending emails, can run over SSL/TLS as SMTPS. Though it usually operates on other ports (e.g., 465), Port 443 is an alternative in environments with strict restrictions.
- Custom protocols and services: Proprietary applications and services, particularly in IoT and enterprise settings, often configure their secure communication to use Port 443 for its ubiquity and ability to bypass firewalls.
Is Port 443 Safe?
Port 443 is widely considered safe because it encrypts web traffic using SSL/TLS, making it the standard for secure HTTPS communication. However, like any technology, Port 443 has potential vulnerabilities. Misconfigured servers, outdated SSL/TLS protocols, and targeted attacks can expose users to risks. Understanding these vulnerabilities and implementing best practices ensures that Port 443 remains a secure gateway for online communication.
Common vulnerabilities of Port 443
Despite its reputation for security, Port 443 is not invulnerable. Attackers can exploit weak configurations, outdated protocols, or improper security measures. Here are some common threats:
- Man-in-the-Middle (MiTM) attacks: A MiTM attack occurs when a malicious actor intercepts communication between a client and a server. By posing as a legitimate endpoint, attackers can gain unauthorized access to sensitive data, such as login credentials or financial information.
- SSL/TLS vulnerabilities: Older versions of SSL/TLS, like those affected by the Heartbleed bug, are prone to exploitation. These vulnerabilities can expose private keys, allowing attackers to decrypt encrypted data. Modern protocols such as TLS 1.3 address these issues, but not all systems have upgraded.
- Malware exploits: Attackers may seek to exploit open ports, including port 443, as a means to infiltrate systems with malware. This can lead to a range of detrimental consequences, including data breaches and system compromise.
- Certificate spoofing: If attackers successfully forge a certificate, they can trick users into connecting to malicious websites. This compromises the integrity of encrypted communication.
Real-world attacks exploiting Port 443
Cybercriminals frequently attempt to exploit vulnerabilities in Port 443 for financial gain, surveillance, or system compromise. Some notable cases include:
- Heartbleed exploits: After the discovery of the Heartbleed bug, attackers exploited vulnerable systems to steal sensitive data from servers. Many organizations were forced to revoke and replace their SSL/TLS certificates.
- Phishing campaigns: Hackers have used forged certificates to create convincing fake websites, tricking users into sharing credentials or payment details.
- Ransomware distribution: Malware like WannaCry has been observed targeting servers through open ports, including Port 443, as part of larger attacks.
Best practices to secure Port 443
Securing Port 443 requires proactive measures to address known vulnerabilities and deter potential attacks. Here are some best practices:
Use modern SSL/TLS protocols
Ensure that your servers use the latest versions of TLS (1.2 or 1.3). Older versions should be disabled to prevent exploitation of known vulnerabilities.
Monitor certificates
Regularly update and monitor SSL/TLS certificates to ensure they remain valid and properly configured. Use Certificate Transparency logs to detect potential spoofing or misissued certificates.
Employ web application firewalls (WAFs)
A WAF can help detect and block malicious traffic targeting Port 443. It acts as an additional layer of defense against exploits and automated attacks.
Restrict access
Limit Port 443 traffic to authorized sources when possible, especially for internal or non-public applications. This reduces the risk of unauthorized access.
Conduct regular security audits
Periodically test your server’s configuration using tools like SSL Labs to identify weaknesses or misconfigurations.
Stay updated
Ensure all software, including web servers and operating systems, is regularly updated to address security patches.
How to open port 443 on your device
Opening port 443 on your device allows specific applications or services to operate smoothly. For example, you might need to open Port 443 if you are:
- Hosting a website or web application using HTTPS.
- Using a remote desktop application to connect to a computer over the internet.
- Using a cloud storage service that uses HTTPS.
- Running a multiplayer game server.
- Sharing files with other computers on your network
While opening Port 443 can be necessary for these scenarios, it’s important to follow the correct steps and manage it securely to protect your system from potential vulnerabilities.
Opening port 443 on Windows
Opening port 443 on Windows is a little more complex than on Mac. That’s because you need to add it to the Windows Firewall directly. To do this:
- Type firewall in the search box, then select Windows Defender Firewall with Advanced Security
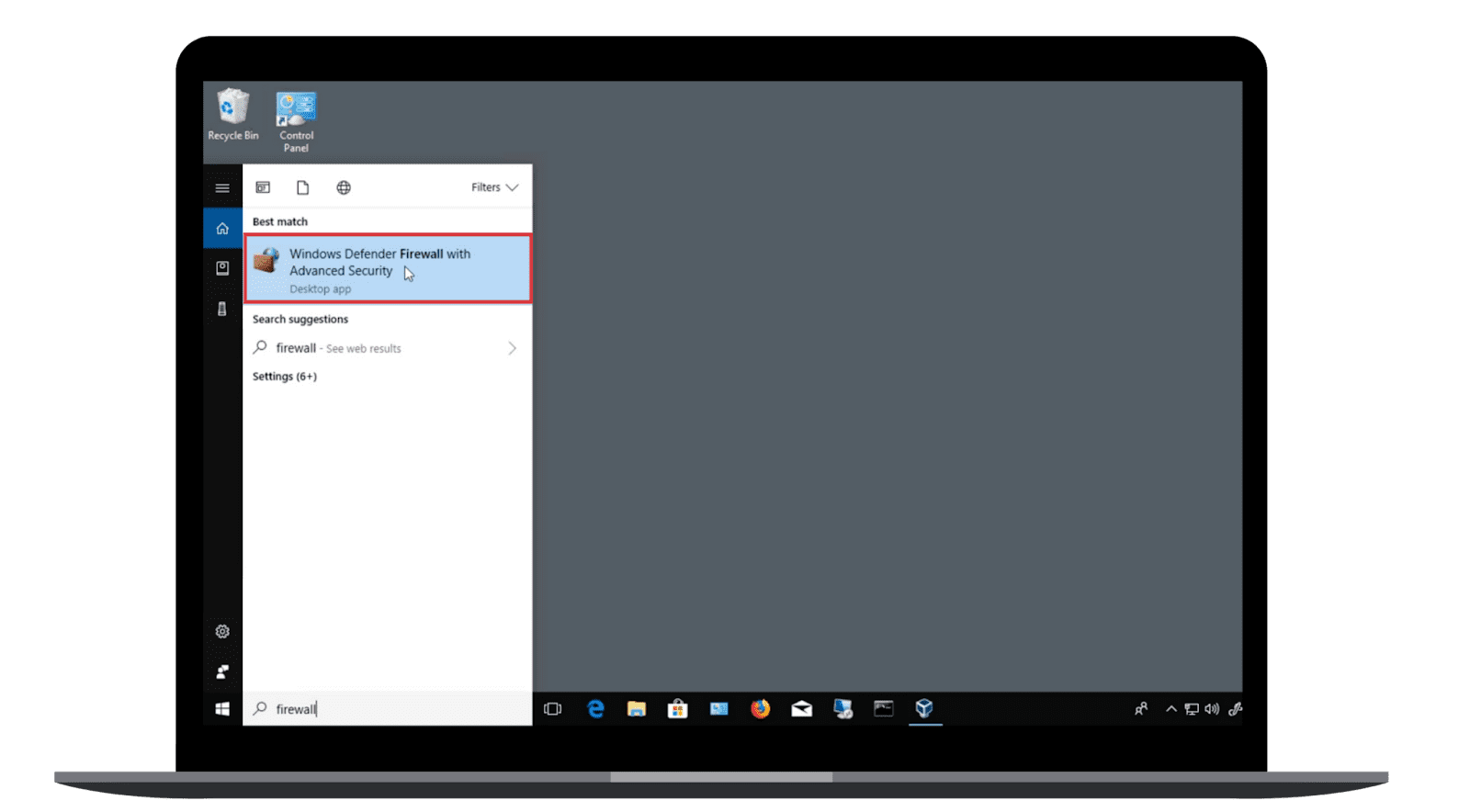
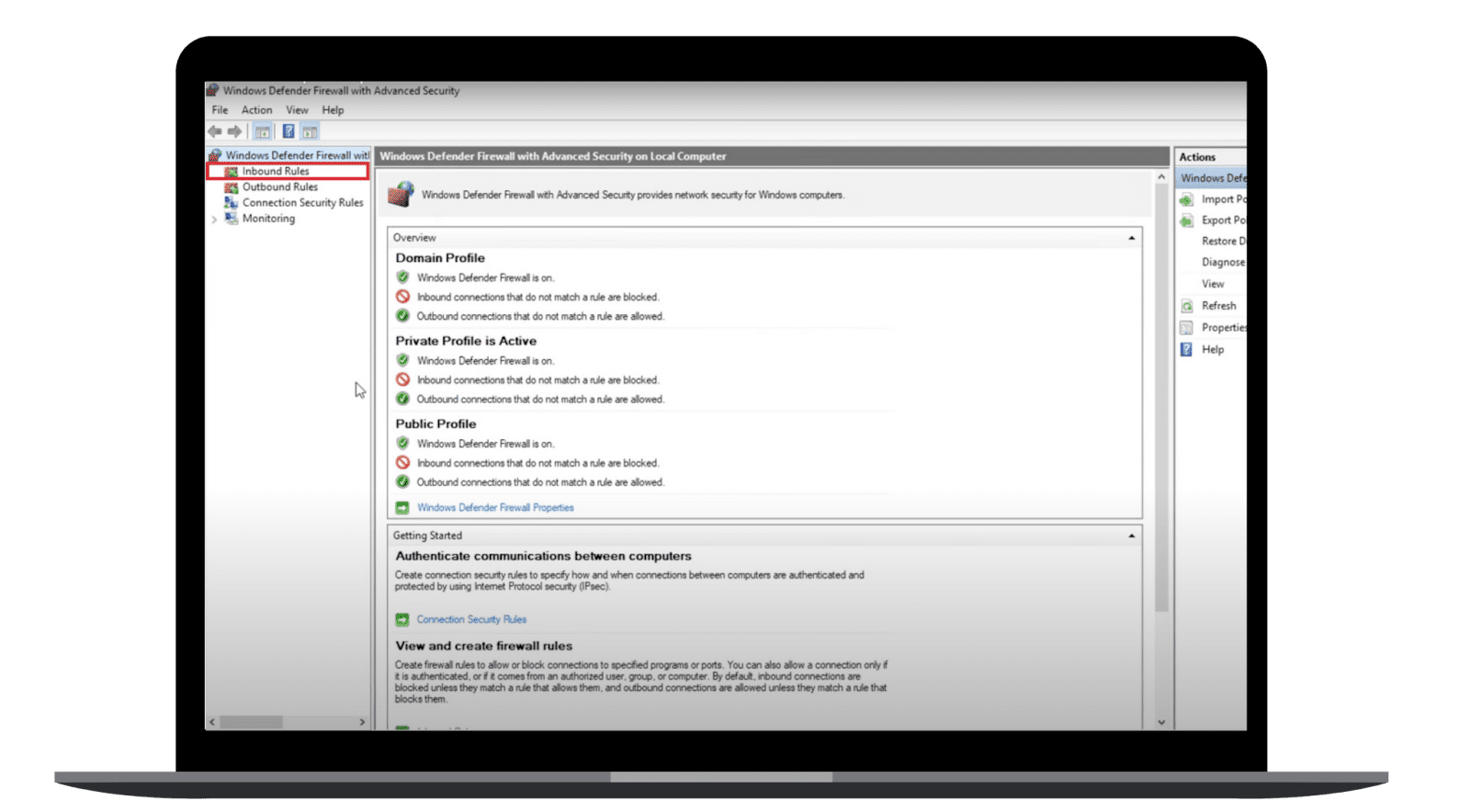
- Once the Windows Firewall is open, in the left pane, select Inbound Rules.
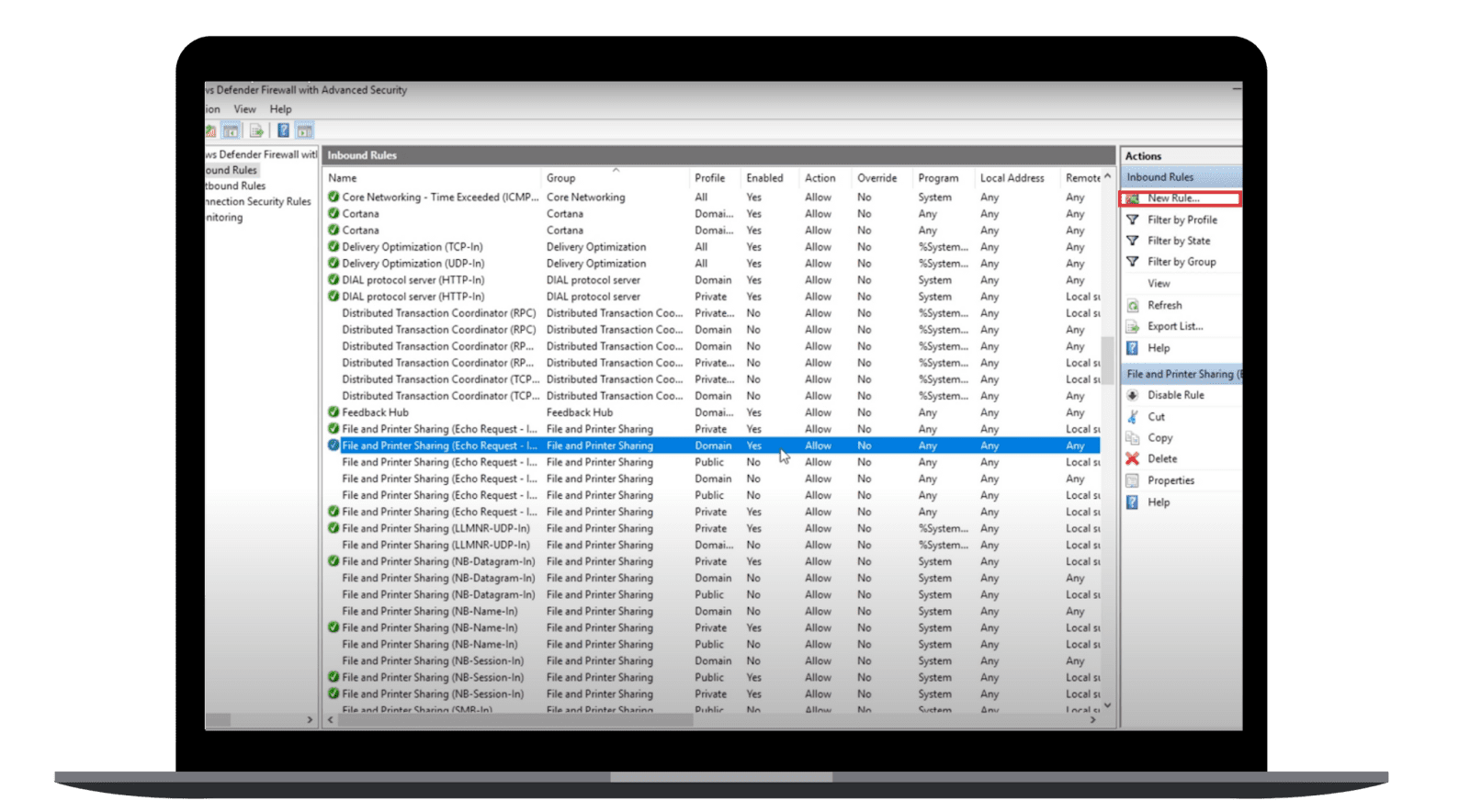
- In the right pane, click New Rule.
- Select Port and click Next.
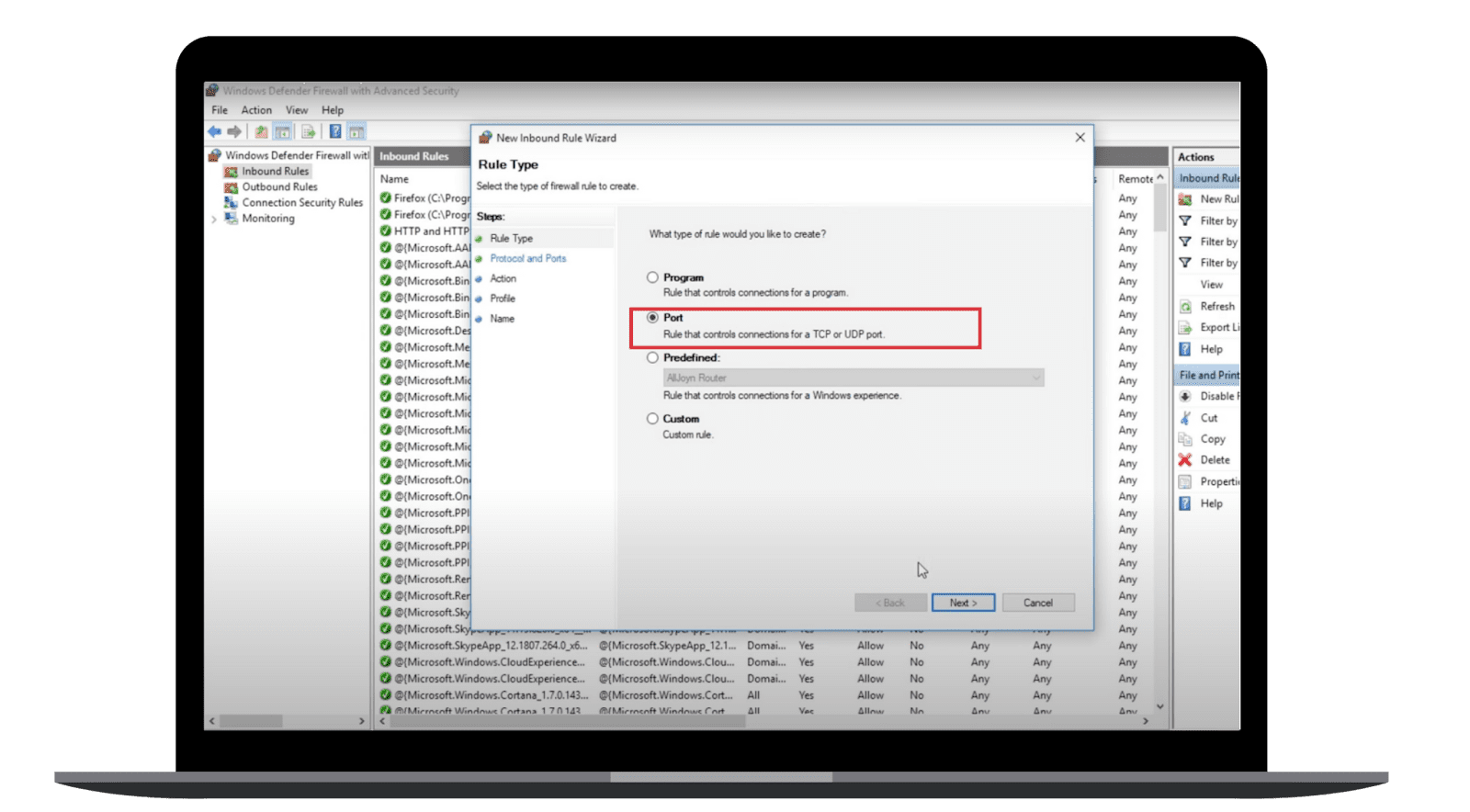
- Select TCP and Specific local ports. In the Specific local ports box, type 443 and click Next.
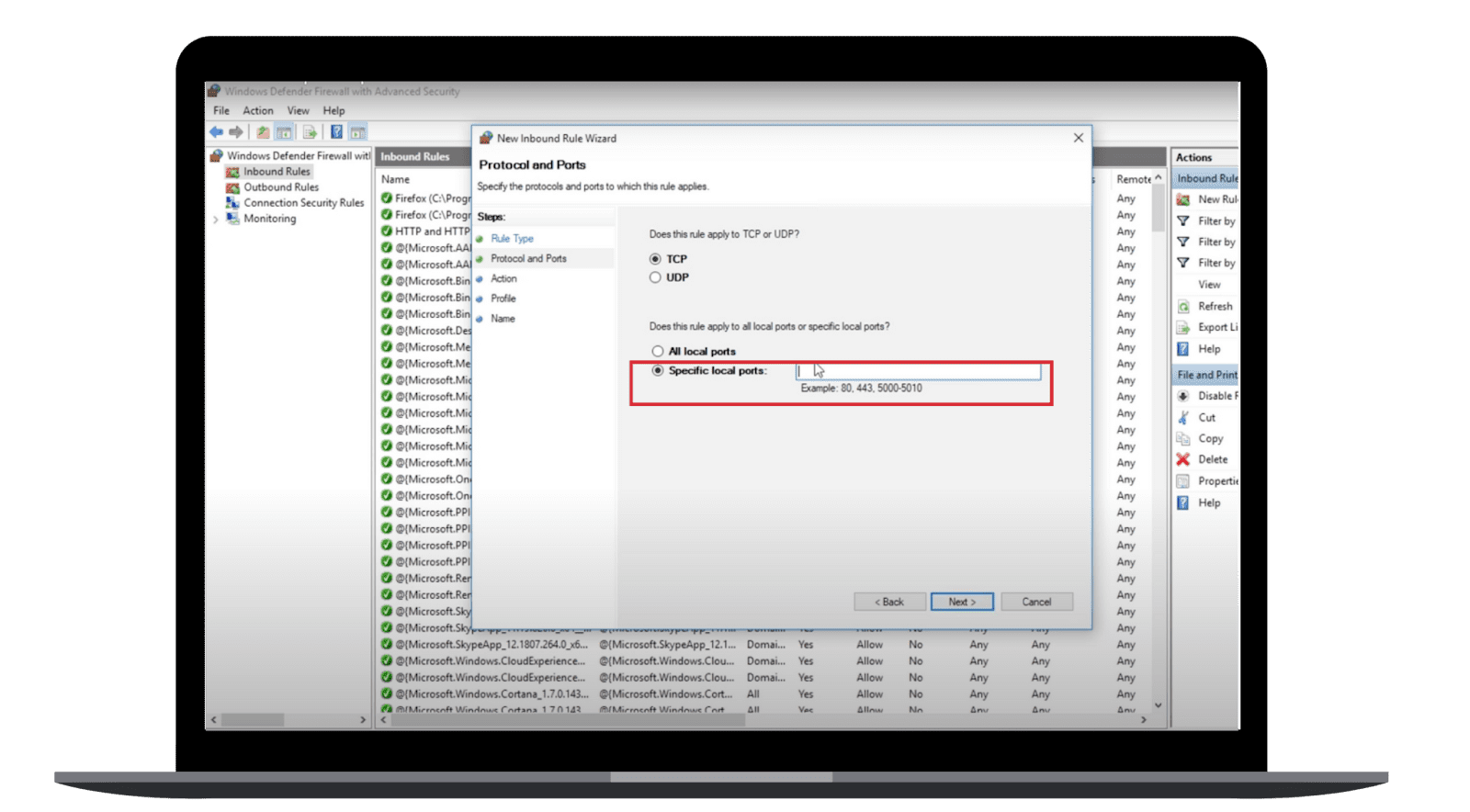
- Select Allow the connection and click Next.
- Select the network profiles that you want the rule to apply to and click Next.
- Give the rule a name and description, and click Finish.
Once you’ve created the rule, port 443 will be open on your computer.
Note: Leaving ports open can increase your computer's vulnerability to attack. Only open ports that you need to open.
Opening port 443 on macOS
To open port 443 on Mac, you follow the steps below. Just ensure your firewall is disabled before you begin.
You can go to System Settings > Network > Firewall to see if yours is on. If it is, turn it off:
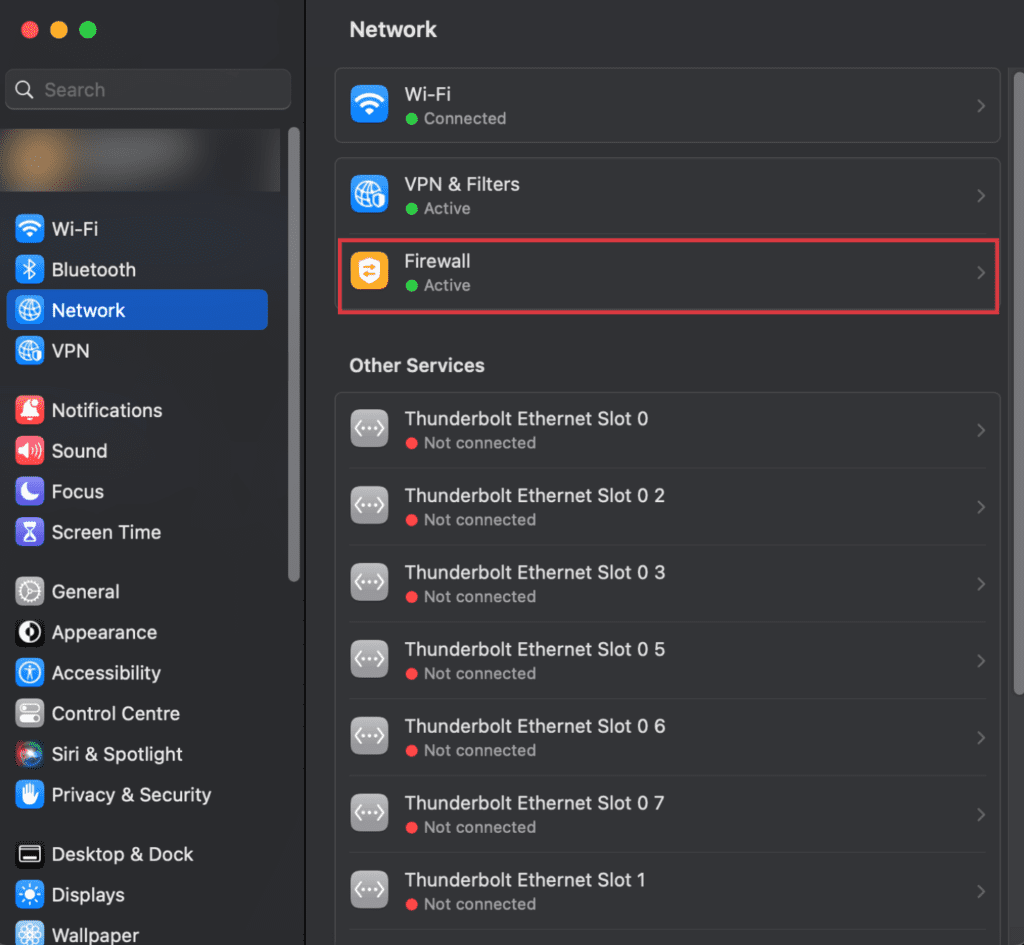
- Then, open the Terminal app.
- At the prompt, enter the following command to stop the packet filler (pf) firewall in case it's active:
-
- sudo pfctl -d
- Open the configuration file for pf by using the nano text editor:
-
- sudo nano /etc/pf.conf
- The editor will show the contents of the default config. To open port 443, enter your custom rule (for example, pass inet proto tcp from any to any port 443 no state) below any existing configurations.
- Press Ctrl-x to exit nano, and press Y and Enter to confirm that you want to save the file with the same name.
-
- Reload the pf firewall rules: sudo pfctl -f /etc/pf.conf
- Lastly, enter the following prompt to re-start the firewall: sudo pfctl -E
Once you’ve opened port 443, applications that need to use it will be able to do so. For example, if you’re running a web server on your Mac, you will need to open port 443 in order for it to be accessible to other devices on the network.
Note: Like with Windows, leaving ports open can introduce security risks. Use this configuration cautiously and consider enhancing your security with a VPN like ExpressVPN to protect your internet traffic and data.
Troubleshooting Port 443 issues
Encountering issues with Port 443 can disrupt secure connections and prevent certain services from functioning properly. Below are steps to diagnose common problems, apply fixes, and reset configurations as needed.
How to check if Port 443 is blocked
To confirm whether Port 443 is blocked, use these methods:
1. Telnet
Telnet is a network protocol that allows you to test connectivity to a specific port on a server. It’s particularly useful for checking whether Port 443 is open and accessible.
- On macOS: Open the Terminal app and type the following command: nc -zv <IP address or hostname> 443. If the port is open, you’ll see a success message like “Connection to <hostname> port 443 [tcp/https] succeeded.”
- Windows: Open the Command Prompt on your Windows machine and type telnet <IP address or domain name> 443 and press Enter. If Telnet successfully connects, the port is open. If you receive an error message, the port may be blocked. Note: You might need to enable Telnet in Windows settings before using this tool.
Telnet is simple but doesn’t provide detailed troubleshooting insights beyond connectivity status.
2. Browser-based tests
Many online tools let you check Port 443’s status directly from your web browser. These tests are quick and require no technical knowledge.
- How it works: Visit an online port scanner (e.g., YouGetSignal) and enter your IP address and Port 443. The tool will attempt to connect and provide a status message, such as “Open” or “Closed.”
- When to use: Browser-based tests are ideal for quick checks if you suspect issues with a specific port but don’t want to use command-line tools.
- Limitations: These tools rely on external servers to test connectivity, so they might not detect internal firewall rules or ISP-related restrictions.
3. Port Scanners
Advanced users can use network scanning tools like Nmap for more detailed diagnostics. Nmap can detect whether Port 443 is open and provide additional insights, such as the protocol in use or potential security vulnerabilities.
- How to use Nmap: Install Nmap on your system and run the following command in a terminal: nmap -p 443 <IP address>. The scan results will indicate whether the port is open or filtered (blocked by a firewall).
- Advantages: Port scanners are more comprehensive, providing additional data about the service running on the port and potential misconfigurations.
Common issues with Port 443 and their fixes
1. Misconfigured firewalls
Firewalls are designed to block unauthorized traffic, but improper configurations can unintentionally restrict access to Port 443.
How to fix:
- Check your firewall settings to ensure Port 443 is allowed:
-
- On macOS: Go to System Preferences > Security & Privacy > Firewall Options and confirm rules for HTTPS traffic.
- On Windows: Open Windows Defender Firewall and check the Inbound Rules for HTTPS or Port 443. Add a new rule if needed.
- Ensure no conflicting rules block the port. For example, "Deny" rules can override "Allow" rules for the same port.
Tip: If you’re managing a network, verify configurations on both device-level and network firewalls, such as those on routers or corporate systems.
2. Outdated SSL/TLS Certificates
SSL/TLS certificates validate secure connections on Port 443. Expired or improperly configured certificates can cause errors.
- Symptoms: Users might see warnings like “Your connection is not private” or experience failed HTTPS connections.
- How to Fix:
-
- Ensure the server has a valid, up-to-date SSL/TLS certificate.
- Use tools like SSL Labs to test certificate configurations and identify issues.
- Upgrade to modern protocols (TLS 1.2 or 1.3) and disable outdated ones (like SSL 3.0 or TLS 1.0) to prevent vulnerabilities.
Tip: Regularly monitor certificate expiration dates and set reminders for renewals.
3. ISP restrictions or throttling
Some Internet Service Providers (ISPs) may restrict or throttle traffic over Port 443, particularly in regions with censorship or during high usage periods.
- Symptoms: Slow or blocked access to HTTPS websites, despite other internet activities working normally.
- How to Fix:
-
- Contact your ISP: Confirm whether restrictions are in place for secure traffic.
- Use a VPN: VPNs encrypt traffic and reroute it through secure servers, bypassing ISP-level restrictions. Ensure your VPN uses Port 443 to blend with regular HTTPS traffic.
- Test connectivity: Use online tools or network monitoring software to check for throttling patterns.
4. Proxy server issues
Proxy servers may block or fail to forward Port 443 traffic correctly due to misconfigurations.
- How to Fix:
-
- Check your proxy settings to ensure Port 443 traffic is allowed.
- On Windows: Navigate to Internet Options > Connections > LAN settings and verify your proxy server configuration.
- On macOS: Go to System Preferences > Network > Advanced > Proxies and ensure HTTPS traffic is routed properly.
5. Application-level conflicts
Sometimes, the application using Port 443 may be the source of the problem. Misconfigurations, bugs, or crashes can prevent connections.
- How to Fix:
-
- Restart the application to clear temporary issues.
- Reinstall or update the application to fix bugs or compatibility problems.
- Check the application's documentation for Port 443-specific requirements.
6. Other quick fixes
- Restart your device: Sometimes, restarting your computer can fix port 443 issues.
- Contact support: If none of these fixes work, reach out to your ISP or the application developer for further guidance.
How to reset port configurations on routers
If you're encountering issues with Port 443 or suspect misconfigured settings, resetting your router's port configurations or firmware can help resolve the problem. Follow these steps:
1. Log in to your router
- Open a web browser and enter your router's IP address (commonly 192.168.1.1 or 192.168.0.1).
- Log in with your admin credentials. If you’ve never changed these, the default username and password can typically be found on the back of your router or in its manual.
2. Check and adjust port settings
Navigate to the Port Forwarding or Firewall section of your router’s admin panel.
- Look for any rules blocking or misrouting Port 443. Delete unnecessary or conflicting rules.
- If you need to enable Port 443, add a new port forwarding rule:
-
- Protocol: TCP
- Port range: 443
- Destination: Your device’s local IP address (e.g., 192.168.1.100)
- Save the rule and restart your router.
3. Reset to default settings (if necessary)
If troubleshooting doesn’t resolve the issue, consider resetting your router to its factory settings.
- Locate the reset button: Usually a small, recessed button on the back of the router.
- Perform a reset:
-
- Press and hold the reset button for 10-30 seconds using a pin or paperclip.
- Release the button when the router restarts (indicated by flashing lights).
- Reconfigure your network: After the reset, log back into the router and set up your network, including any custom rules for Port 443.
4. Update your router’s firmware
Outdated firmware can cause compatibility issues, including problems with Port 443.
- Check for updates:
-
- Look for the Firmware Update section in your router’s admin panel.
- Follow the instructions to download and install the latest version from the manufacturer’s website.
- Updating your firmware often resolves bugs or limitations that could affect port functionality.
5. Test connectivity
After making changes, test Port 443 to ensure it’s accessible:
- Use tools like Telnet, browser-based port scanners, or Nmap to confirm that the port is open and functioning correctly.
6. Contact your ISP (if needed)
If resetting and reconfiguring your router doesn’t resolve the issue, contact your ISP. Some providers block or throttle certain ports, including Port 443. They can help identify and remove any restrictions affecting your connection.
The Importance of Port 443 for VPNs
VPNs heavily rely on Port 443 for its unique advantages, especially in ensuring secure and unrestricted connectivity in challenging environments. As mentioned above, this port helps facilitate the evasion of restrictions and also enhances the overall security and reliability of VPN connections.
Why Port 443 is essential for VPN security
Port 443 supports the secure transmission of data through SSL/TLS encryption, which is critical for VPN traffic. Here’s why it matters for VPN security:
Global compatibility
Since Port 443 is universally used for HTTPS traffic, it provides an optimal pathway for VPNs to function seamlessly across networks without requiring additional configuration or risking blocks.
Data encryption and privacy
VPNs using Port 443 maximize encryption benefits by pairing their tunneling protocols with the same cryptographic protections as HTTPS traffic. This dual layer of encryption ensures both the content and transport of data are secure.
Minimized disruption in complex networks
Whether dealing with corporate proxies, campus firewalls, or restrictive ISP setups, Port 443 ensures uninterrupted VPN functionality where other ports may fail due to lack of universal acceptance.
How ExpressVPN leverages Port 443 for seamless connectivity
ExpressVPN takes full advantage of port 443 to optimize its performance in restrictive networks while prioritizing user security. As port 443 is the standard for HTTPS traffic, it ensures VPN connections blend seamlessly with regular encrypted web activity, making them nearly indistinguishable from standard online browsing. This offers three key benefits:
Reliable access in restrictive networks
For users in heavily censored regions, where governments or ISPs attempt to block VPNs, port 443 serves as a lifeline. Because this port is essential for web browsing and online services, blocking it would disrupt core internet functionality. ExpressVPN leverages this by tunneling VPN traffic through port 443, allowing users to bypass strict firewalls and regain access to censored content or services.
Enhanced privacy and stealth
By disguising VPN traffic as HTTPS data, ExpressVPN minimizes the risk of detection through deep packet inspection (DPI). This not only protects user privacy but also ensures stable connections even on networks with active monitoring. The encryption protocols employed by ExpressVPN on port 443 provide additional security, safeguarding sensitive data from interception.
Optimized performance across devices
ExpressVPN’s integration with port 443 isn’t limited to bypassing restrictions. It’s also optimized for performance across a variety of devices and operating systems. Whether users are on mobile, desktop, or connected through a router, port 443 ensures compatibility and speed without sacrificing security.
Final thoughts on Port 443
Port 443 plays a foundational role in modern internet security, enabling secure communication through HTTPS and protecting sensitive data like login credentials, payment information, and personal details.
This port is particularly essential for secure browsing and services requiring encryption, such as online banking, e-commerce, and healthcare platforms. Its utility extends beyond web browsing, supporting APIs, cloud storage, and remote access tools. For VPNs, Port 443 offers a reliable channel for bypassing restrictions in censored environments while maintaining user privacy and security.
However, Port 443 isn’t without its challenges. Misconfigured systems, outdated SSL/TLS protocols, and unmonitored vulnerabilities can leave it open to exploitation. Organizations and individuals must ensure they adopt the latest encryption standards, routinely audit configurations, and address potential weaknesses to maximize security.
Ultimately, Port 443 is a cornerstone of online safety. While it facilitates secure, encrypted communication for billions of users every day, maintaining its integrity requires proactive measures to stay ahead of evolving cyber threats.
FAQ: About port 443
What is 443 port used for?
Is HTTPS always port 443?
What's the difference between port 80 and port 443?
Is it OK to have port 443 open?
Can port 443 be blocked?
How do I know if my firewall is blocking port 443?
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN