The ultimate guide to phone security: How to protect your mobile device

You probably start your day by grabbing your phone. It’s where you check messages, manage money, snap photos, store tickets, and even get work done. With so much packed into one device, it’s no surprise that phones are a prime target for thieves and scammers. The good news is you don’t need fancy tech skills to stay safe. What you need is a simple, realistic plan.
In this guide, we’ll walk you through practical, easy-to-follow steps to keep your phone safe from today’s most common threats without losing the convenience that makes it so essential in daily life.
What is mobile phone security, and why does it matter?
Mobile phone security is the set of tools and practices that protect your device and the information on it from different threats, like malware, hacking, data leaks, or even loss and theft.
What does phone security include?
Protecting your phone requires attention to several areas. These aren’t an official standard, but thinking of them as pillars helps organize the main risks and defenses into a clear, practical framework for your digital life:
- Device hardening: This refers to the safeguards built into the physical phone itself. It involves mechanisms like screen locks, biometric authentication, storage encryption, and remote “find/lock/wipe” functions that protect the device if it’s lost or stolen.
- Account hardening: It focuses on the digital identities linked to the phone. This includes the use of secure login methods such as passkeys and multi-factor authentication to keep services like email, banking, and social media safe from unauthorized access.
- Mobile app security: This governs the software you install. It’s generally advisable to download apps from trusted sources, carefully review app permissions, and keep them updated to prevent malware from gaining a foothold on your device. Play Protect and App Store reviews are guardrails, not guarantees.
- Network hygiene: The emphasis here is on internet connections. Safe practices and encryption technologies, such as virtual private networks (VPNs), help reduce the dangers of unsecured networks and potential interception of online activity.
Who needs phone security and why?
Simply put, anyone who owns a smartphone needs phone security. Whether you’re a student connecting to public Wi-Fi, a professional checking work email on the go, or someone who just wants to keep personal photos and banking apps private, your phone is a target.
Cybercriminals rely on scale. Automated attacks try millions of stolen passwords, and malware hides in shady apps downloaded thousands of times. At the same time, everyday risks remain, like losing an unlocked phone on the train or having it snatched in a crowded bar.
And it’s not just about personal use. For businesses, each phone is part of the larger security picture. A compromised device can give attackers a way into company email, shared files, or cloud services.
The most common mobile security threats
Mobile threats often follow familiar patterns. The key to protecting yourself is learning to recognize those patterns early so you can spot risks quickly and react before they cause harm.
1. Malware and viruses
Malware is a general term for harmful software, with viruses being one of its best-known types. It can reach your phone through sideloaded apps, malicious ads, or abused permissions. Once installed, it might disguise itself as a trusted app, steal login details, intercept security codes, or spy on the victim (in the case of banking trojans or stalkerware).
The scale of the problem is significant. In 2024, Google Play Protect’s real-time scanning detected over 13 million new malicious apps outside the Play Store. Security firm Zimperium likewise reported a surge in mobile banking trojans between 2022 and 2023, with the number of malware families targeting banking apps nearly tripling from 10 to 29.
2. App-based threats and spyware
Many mobile threats come from the apps that users install themselves, and they usually fall into three groups.
Some apps are overprivileged, asking for more access than they need, like a game requesting access to contacts or microphone. Others are simply insecure, with weak coding or poor data handling that might leave users’ information exposed. And some are outright malicious, such as spyware that secretly tracks location, messages, calls, or keystrokes and sends the data to third parties.
3. Wi-Fi and network vulnerabilities
Public Wi-Fi in places like cafés, airports, and hotels is convenient, but it often lacks proper security. Attackers can create evil twin hotspots with names that look legitimate (like “Hotel Guest Wi-Fi”). Once connected, they launch man-in-the-middle (MITM) attacks, intercepting or altering network traffic.
Another common risk is session hijacking, where attackers steal cookies or session tokens to impersonate the victim online. Even though most modern apps and websites use HTTPS, a malicious hotspot or poorly configured connection can still put user accounts and data at risk.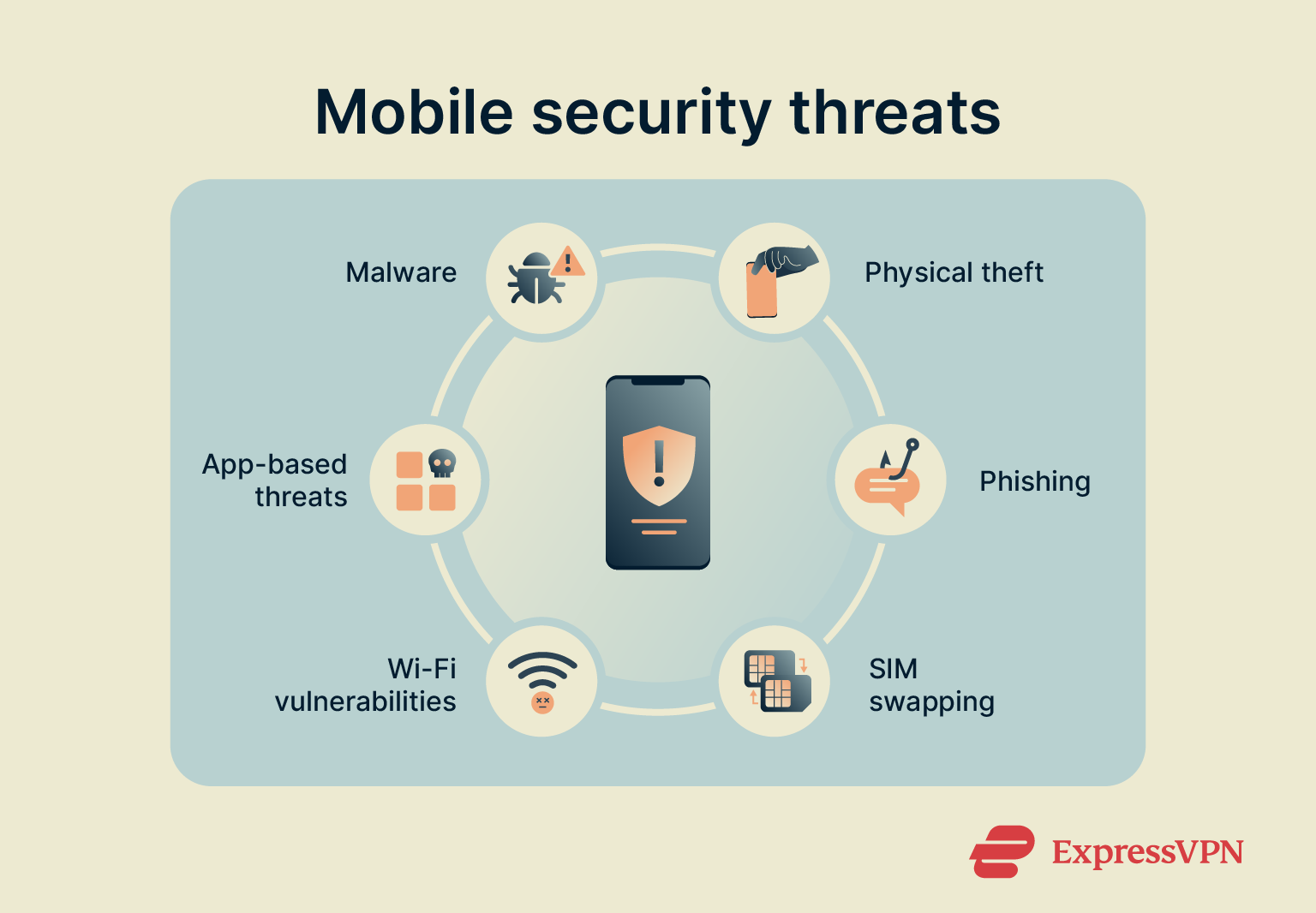
4. SIM card attacks and SIM swapping
Attackers may clone a SIM card if they get physical access, copying its data onto another card under their control. The more common threat, however, is SIM swapping (or SIM card fraud), when someone tricks a mobile carrier into transferring a phone number to a SIM they control. Once that happens, they receive the victim’s calls and SMS messages, including one-time passcodes and recovery links.
Another risk comes from the outdated Signaling System No. 7 (SS7) protocol, which phone networks still use to route calls and texts. Because it lacks modern safeguards, attackers with network access can intercept messages, eavesdrop on calls, or track a phone’s location. While users can’t prevent SS7 attacks themselves, it’s a reminder of how old telecom systems still pose security risks.
5. Phishing and social engineering
Social engineering tricks people into revealing sensitive information, and the most common method is phishing. On phones, this often appears as a text (smishing) or a message that creates urgency, like claiming an account is locked or a package is waiting.
The link leads to a fake site that looks legitimate, where entering sensitive details hands them to the attacker. Small screens and quick taps make spotting these scams even harder on mobile devices.
6. Physical threats
Not all attacks are digital; sometimes the simplest ones are the most effective. Criminals may first shoulder surf, watching the victim type their PIN in a public place, and then follow up with theft, stealing their phone moments later. With both the device and the code, criminals can quickly unlock apps, access accounts, and cause damage before the victim can react.
How to secure your phone
If you want to keep your phone safe, the secret is layers. Think of security like stacking shields; each layer covers the gaps in the others. Together, they create overlapping defenses that make it much harder for attackers to break through.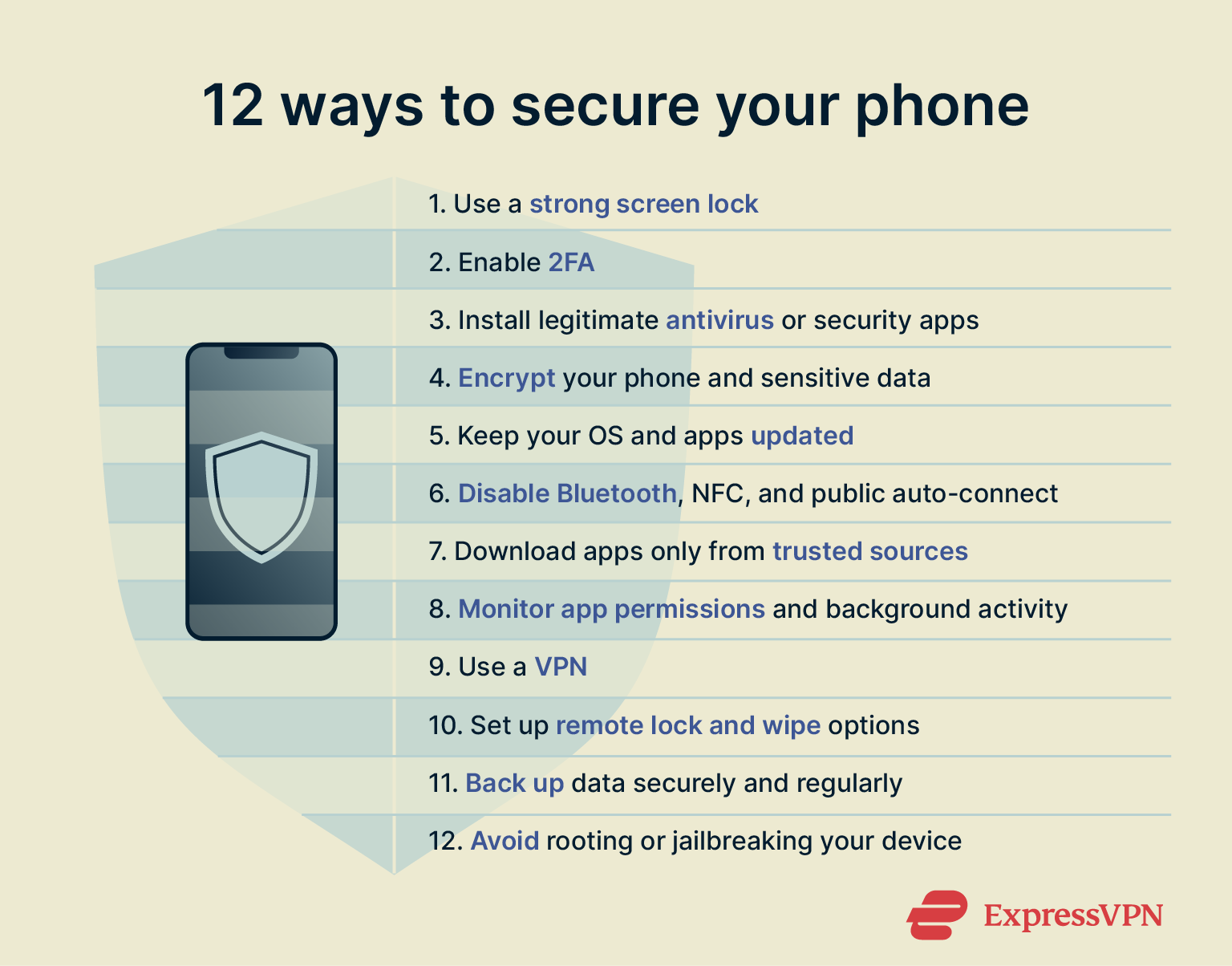
1. Use a strong screen lock
Your lock screen is the first and most important defense for your phone. A simple swipe or weak pattern is easy to bypass, but a strong PIN or password creates a barrier that attackers can’t realistically break without knowing it.
Many phones also offer biometrics, like fingerprints or facial recognition. These are mainly convenience features, but not a replacement for a strong PIN or password because the level of security they provide is much lower.
2. Enable 2FA
Two-factor authentication (2FA) adds an extra check when you log in, so even if someone steals your password, they can’t access your account. Turn it on for key accounts like email, banking, and cloud storage.
It’s best to use an authenticator app or passkeys instead of SMS codes, which can be hijacked in a SIM swap attack. Store any remaining passwords in a trustworthy password manager like ExpressVPN Keys so they’re long and unique. For maximum protection, consider a hardware key (like a YubiKey), which works with USB-C or near-field communication (NFC) on most phones.
3. Install legitimate antivirus
Antivirus software is designed to detect and block malicious files, phishing attempts, and spyware before they compromise your device. On mobile, a good antivirus can alert you to phishing attempts and scan apps, links, and downloads to flag dangerous behavior, giving you protection beyond the phone’s built-in defenses.
4. Encrypt your phone and sensitive data
On Android, encryption is enabled by default once you set a lock screen with a PIN, password, or biometric, ensuring your files can’t be read without your credentials. On iPhone, follow this guide to enable end-to-end encryption (E2EE) of the data stored on your device.
For private conversations, encryption doesn’t stop at your device. Messaging apps like Signal and WhatsApp use E2EE, too, ensuring that only you and the person you’re talking to can read the messages. This makes them a safer choice for sensitive chats compared to unencrypted SMS or standard messaging services.
5. Use a VPN
A virtual private network (VPN) adds protection beyond your phone’s built-in or app-level encryption. Instead of just securing stored data or chats, it encrypts all the traffic leaving your phone.
This is especially important on public Wi-Fi, where attackers might try to snoop on your activity. With a trusted service like ExpressVPN, your connection runs through a secure tunnel that hides your browsing and masks your IP address.
Getting started is simple: download the app, sign in, and connect. From then on, all your mobile traffic is encrypted until you turn it off.
6. Keep your operating system and apps updated
Software updates are one of your most effective defenses. Programs and operating systems can contain security flaws, called vulnerabilities, which cybercriminals exploit to break into devices and steal data.
To counter this, developers release updates that include “patches” to fix these flaws and close the security gaps. That’s why it’s important to enable automatic updates for both your operating system and your apps.
7. Turn off Bluetooth, NFC, and auto-connect on public networks
Your phone’s wireless radios (like Bluetooth and NFC) create an over-the-air attack surface, meaning they are potential entry points for an attacker. When you’re not using them, turn them off.
Remove any old or unfamiliar paired devices, and turn off Wi-Fi auto-connect so your phone doesn’t automatically join a fake hotspot disguised as a trusted network.
8. Download apps only from trusted sources
Apps are one of the biggest ways threats get onto phones. To stay safe, stick to the Google Play Store or Apple’s App Store, where apps go through checks before they’re published.
On Android, Google Play Protect also scans apps in the background and warns you if something looks harmful. Sideloading from random websites or unofficial stores bypasses these protections and makes it far easier to end up with malware.
9. Monitor app permissions and background activity
When you install an app, it asks for permission to access parts of your phone, like your camera, microphone, or location. Follow the principle of least privilege: an app should only have the permissions it absolutely needs to do its job.
A calculator app, for example, has no reason to request your location. Regularly review app permissions in your phone’s settings and revoke any that seem excessive.
On Android
- Go to Settings and select Apps.
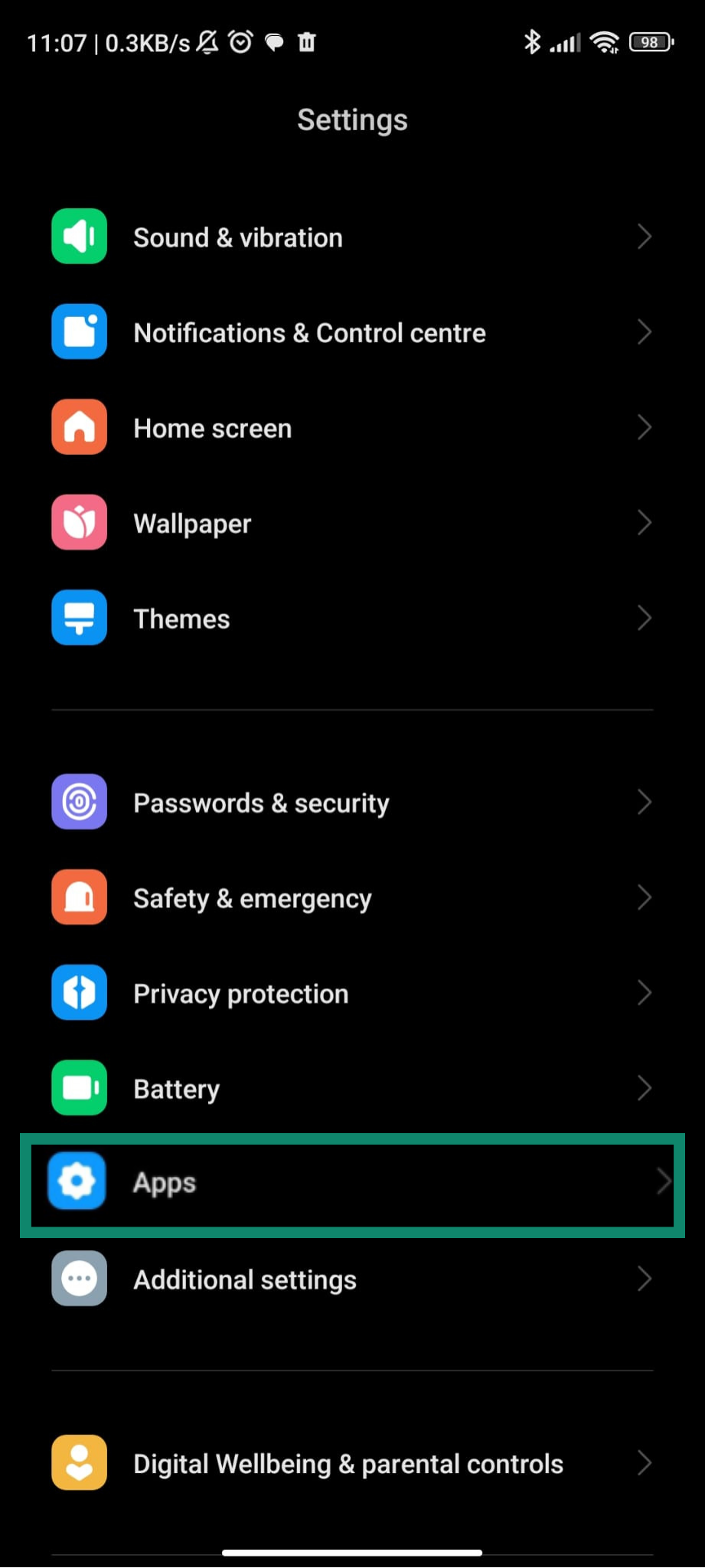
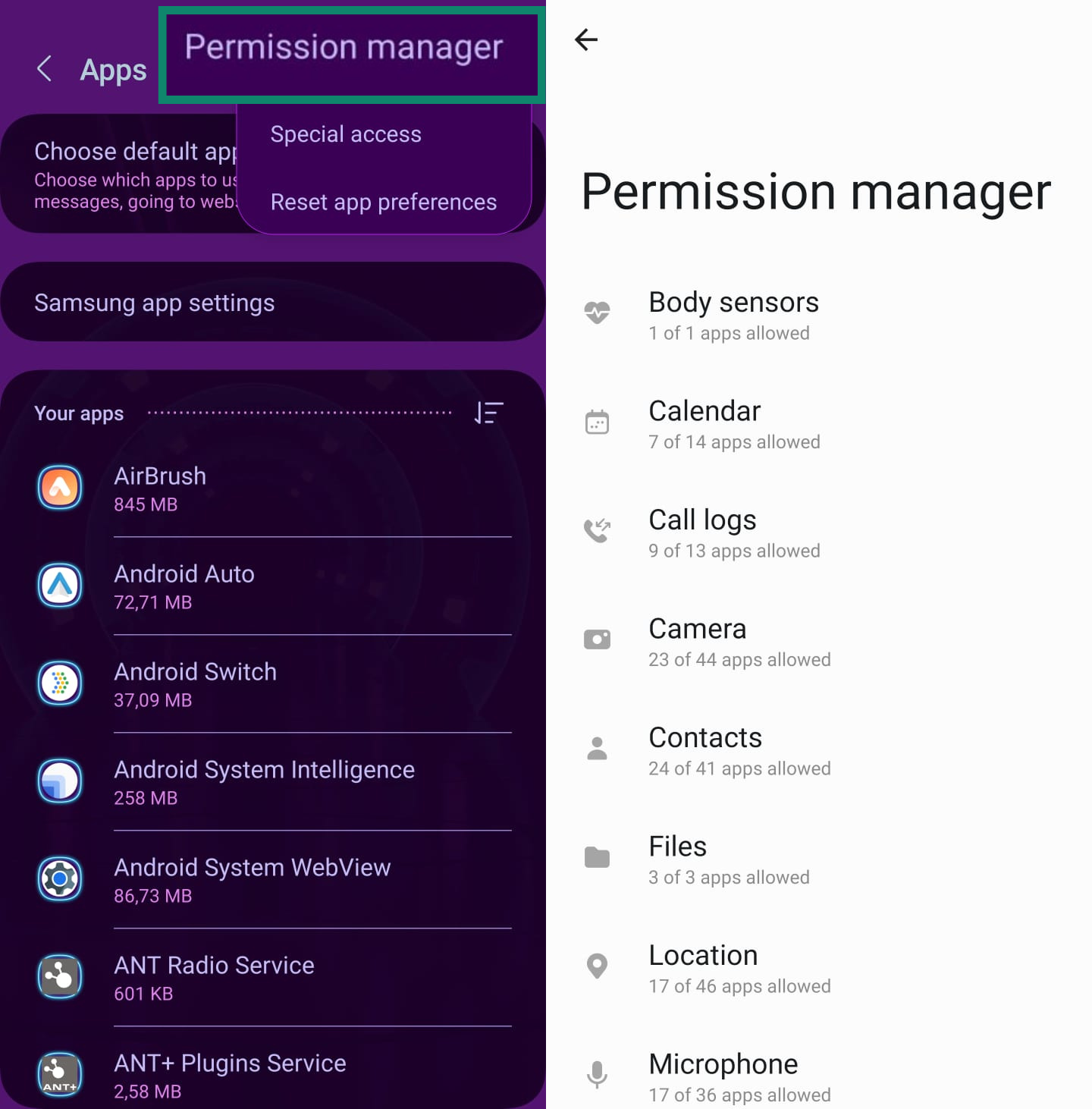
- Depending on the Android model, click More (or Permissions) and choose Permission manager. Revoke permissions that look excessive.
On iPhone
- Open Settings and go to Privacy & Security.
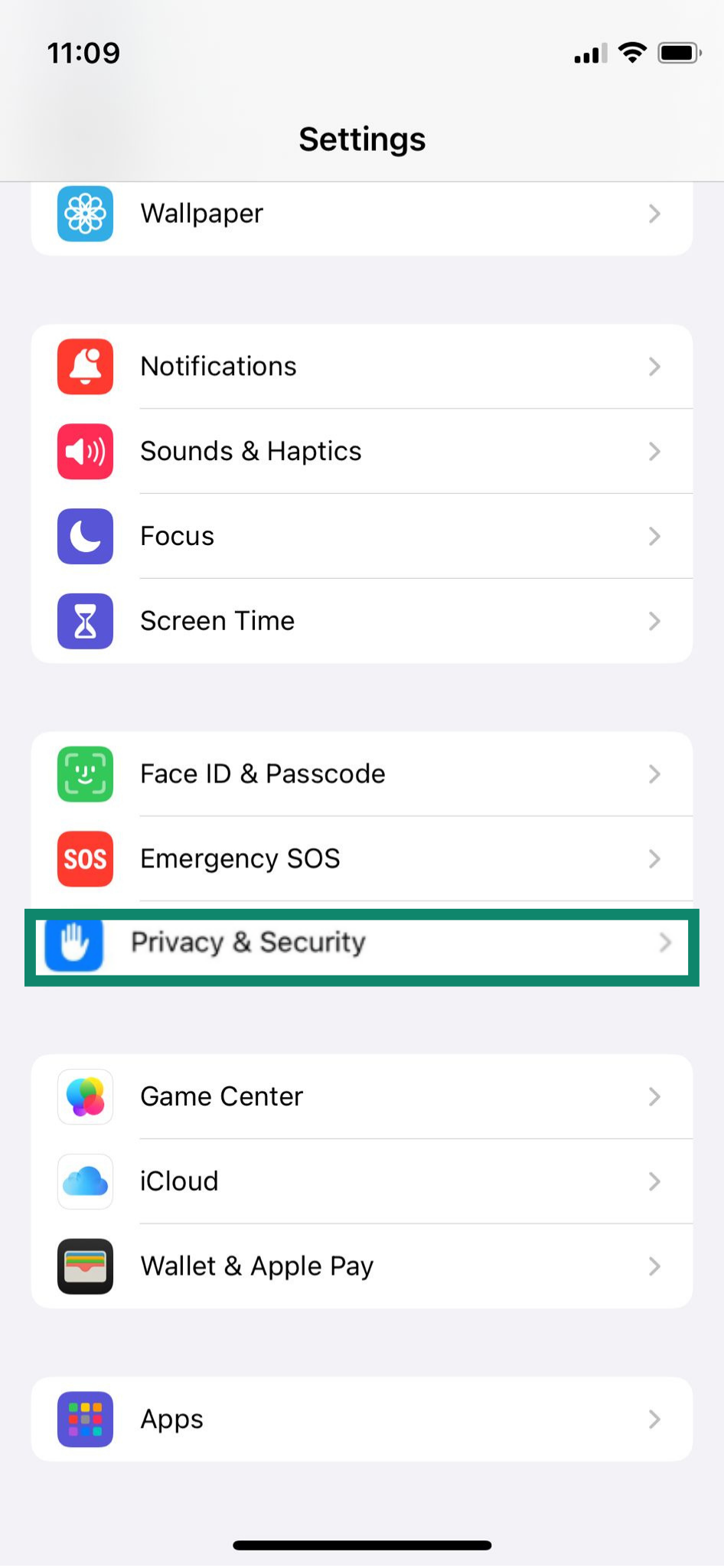
- Choose Location Services and revoke permissions for apps that don’t need to know your location.
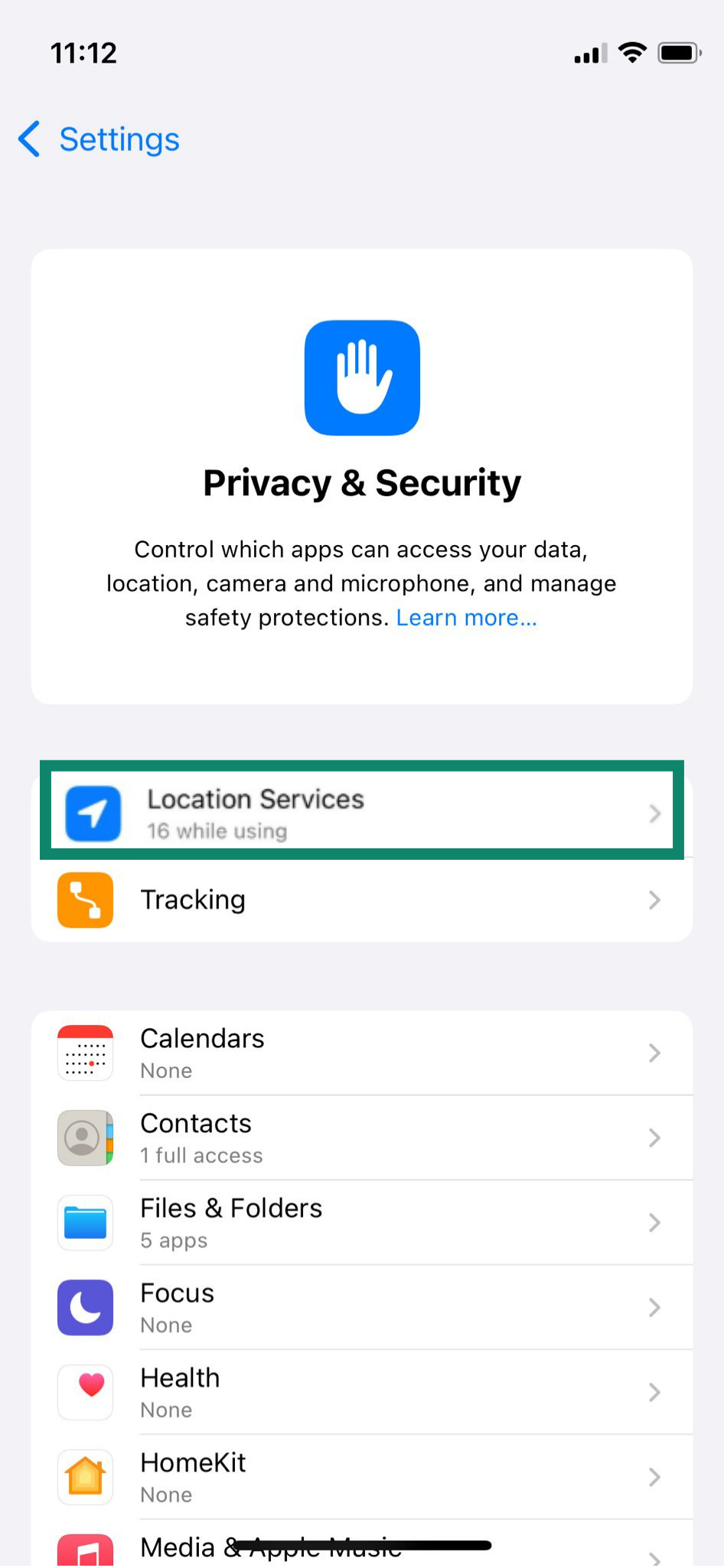
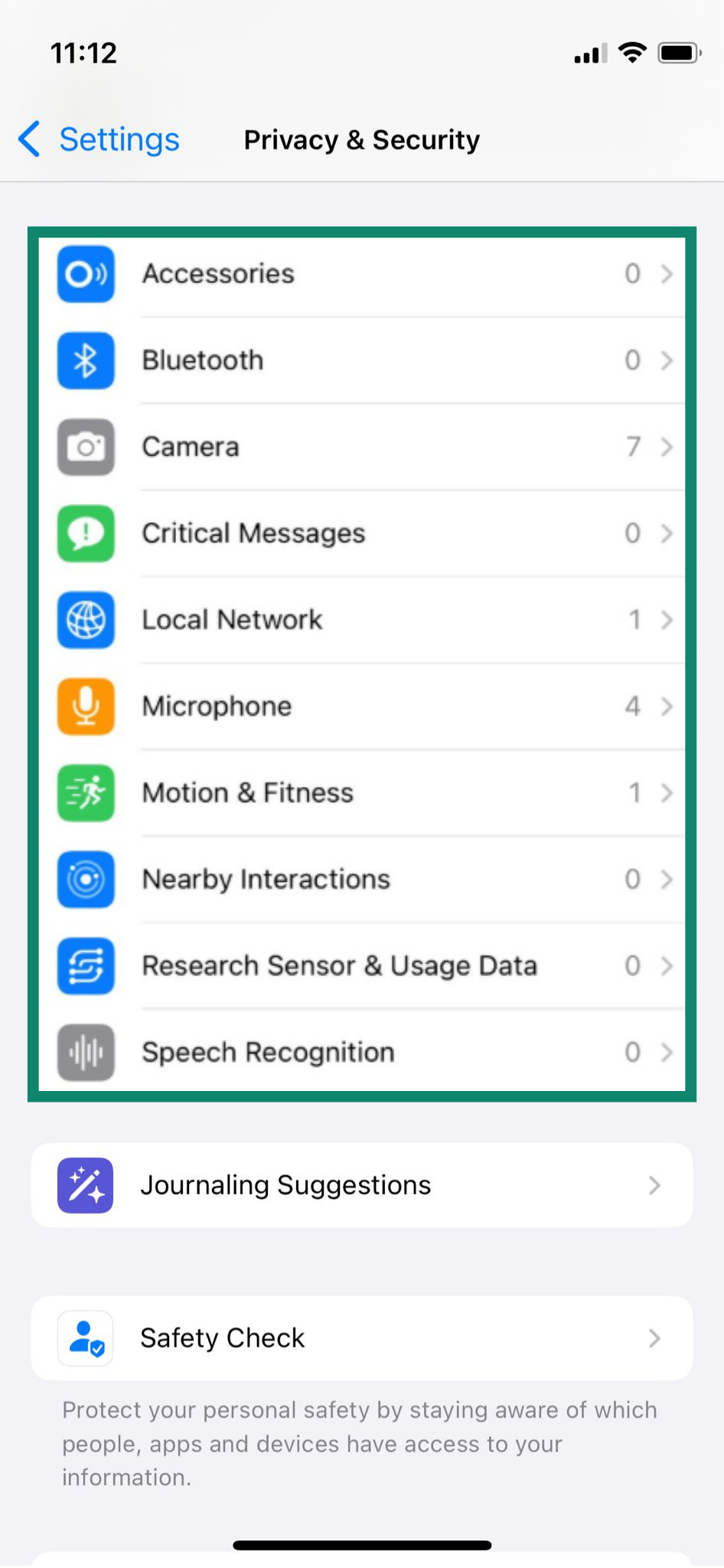
- Go back to Privacy & Security. Scroll down and select options like Bluetooth, Camera, Microphone, etc. to see which apps can use them. Toggle permissions off if needed.
Another option is to go to Settings > Apps, where you can review each app individually and see exactly which permissions it has enabled.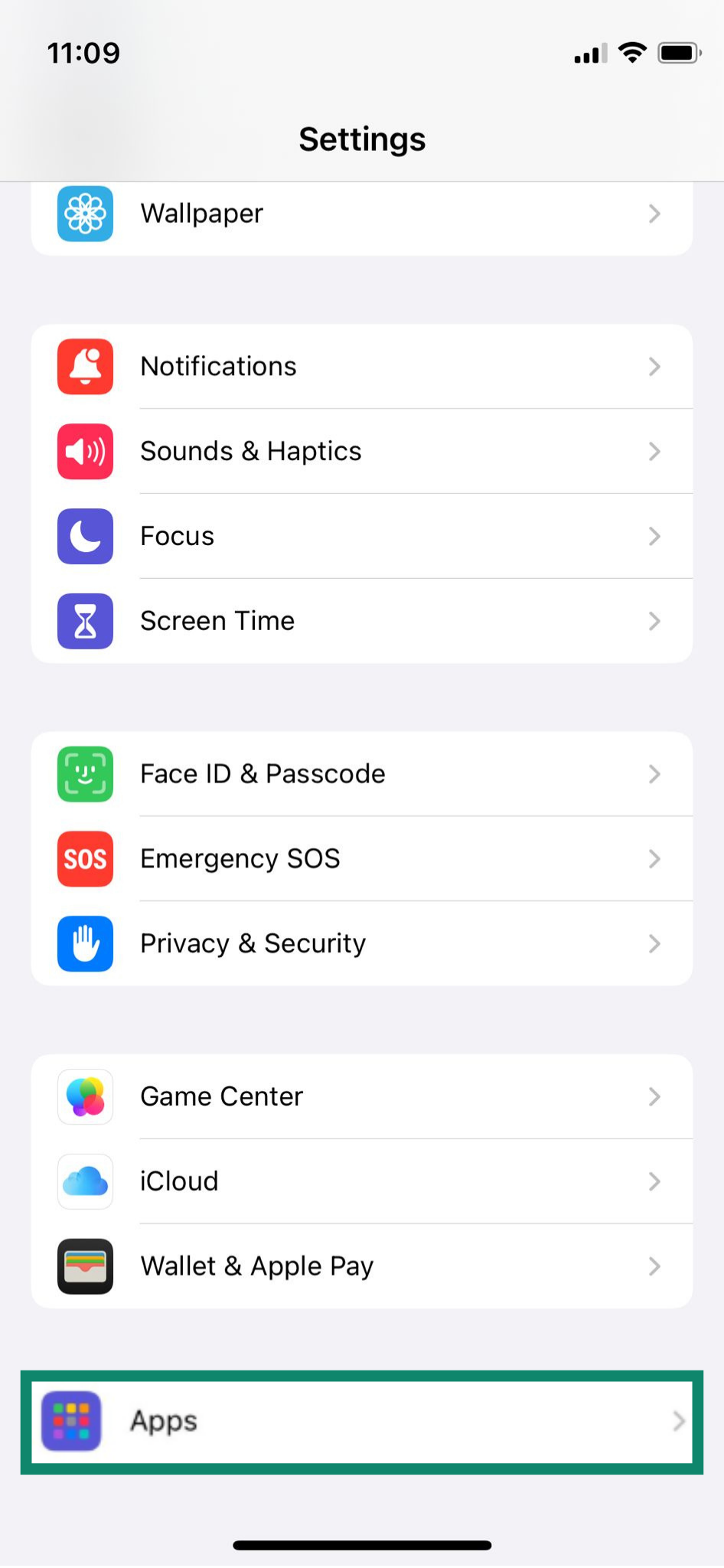
You can also go to Settings > Privacy & Security > App Privacy Report > Turn On App Privacy Report to check how apps use the permissions you’ve granted and what data they access in the background.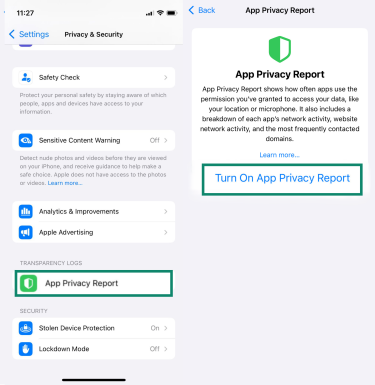
10. Set up remote lock and wipe options
Services like Find My (Apple) and Google’s Find Hub (Android) act as a safety net if your phone is lost or stolen. They let you locate your device on a map, lock it remotely with a custom message, or, if necessary, erase all your personal data. Make sure these features are enabled and test them so you know how they work.
On Android
- Open Settings and go to Security and privacy (on some devices it may be just Security).
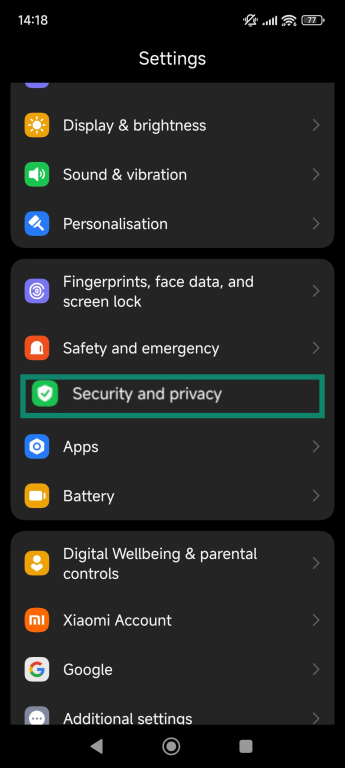
- Tap Find My Device.
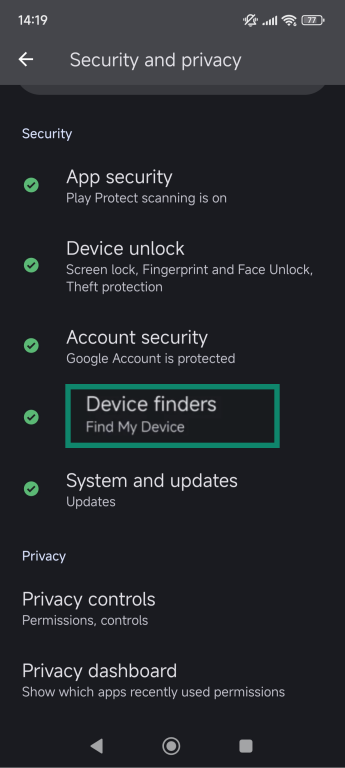
- Turn it on.
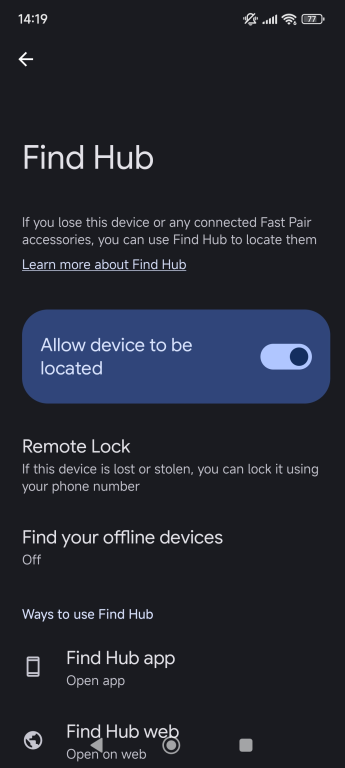
On iPhone
- Open Settings and tap your Apple ID name at the top. Select Find My.
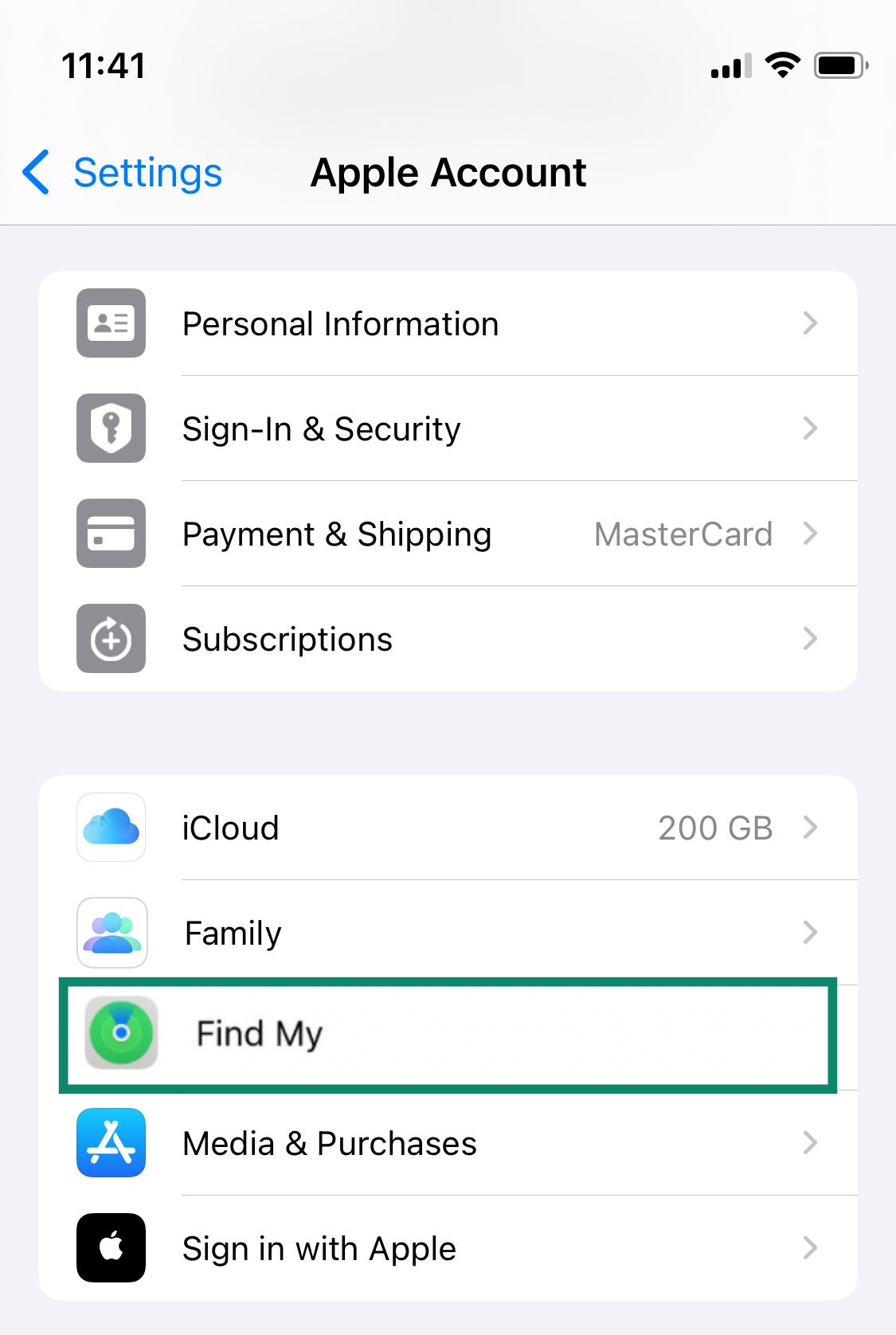
- Tap Find My iPhone.
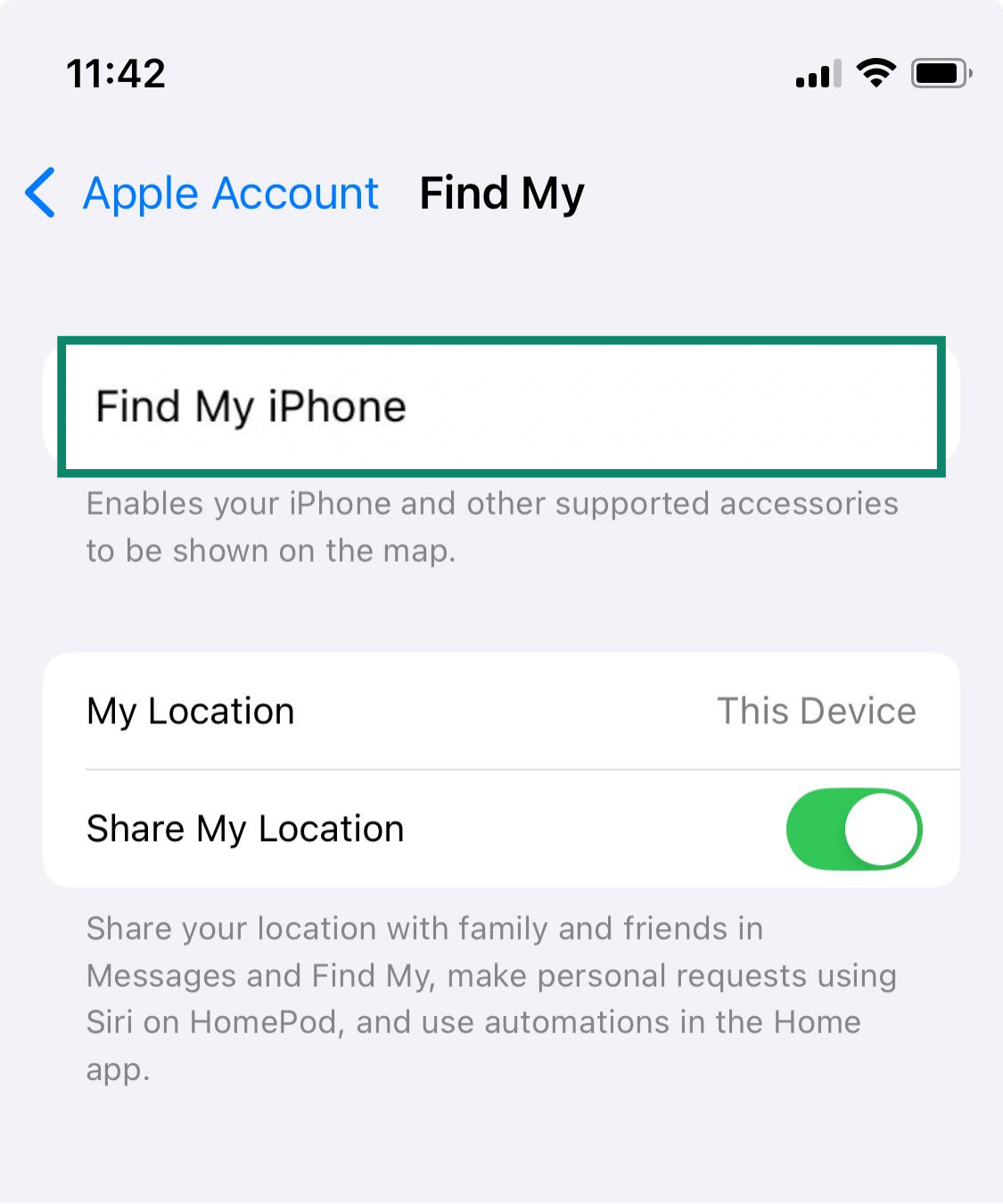
- Toggle on Find My iPhone, Find My network (helps locate even if offline), and Send Last Location (sends the phone’s location to Apple when the battery is low).
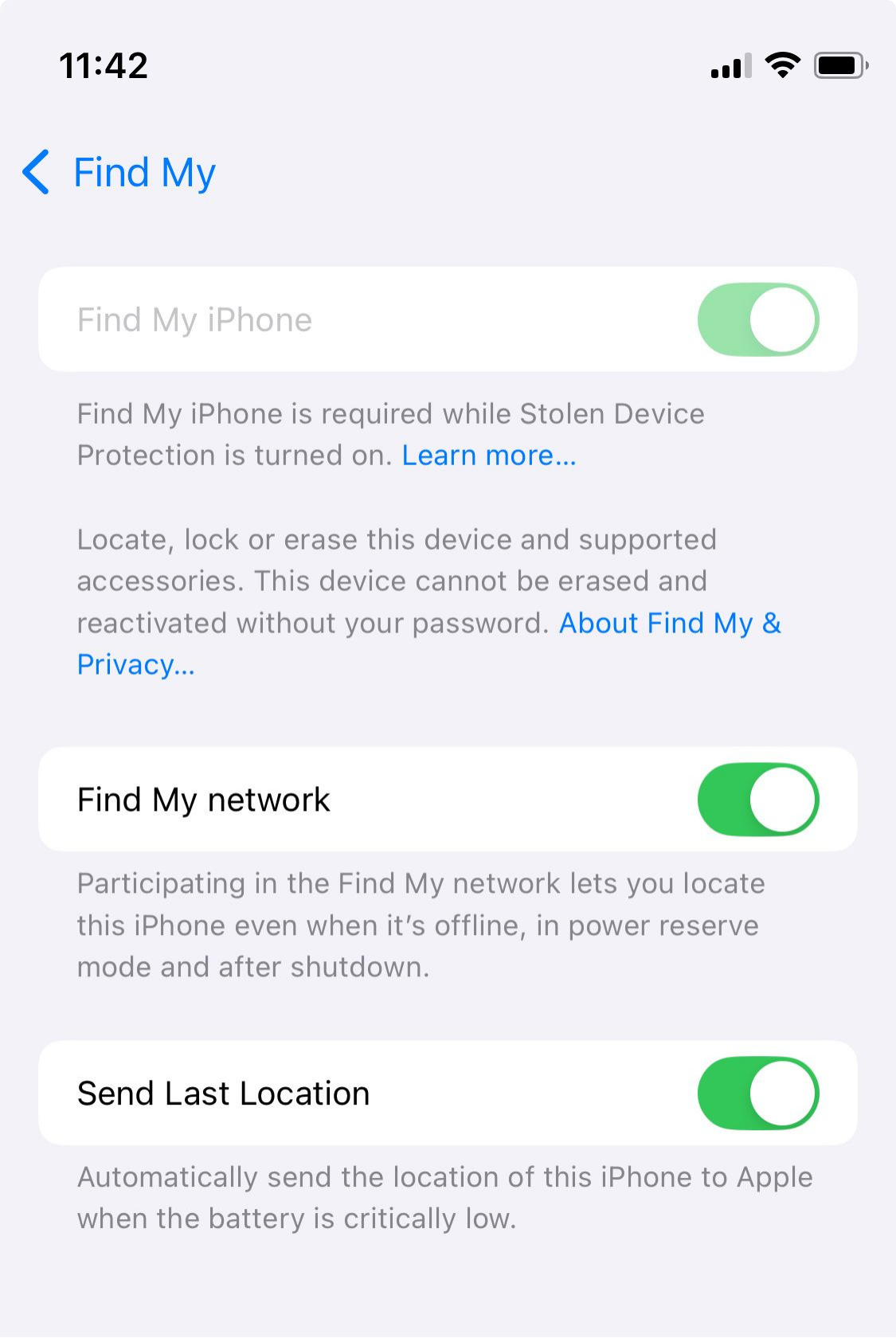
On iPhone, also turn on Stolen Device Protection, which requires biometric verification for sensitive actions when you’re away from trusted locations.
- Open Settings. Scroll down and tap Face ID & Passcode.
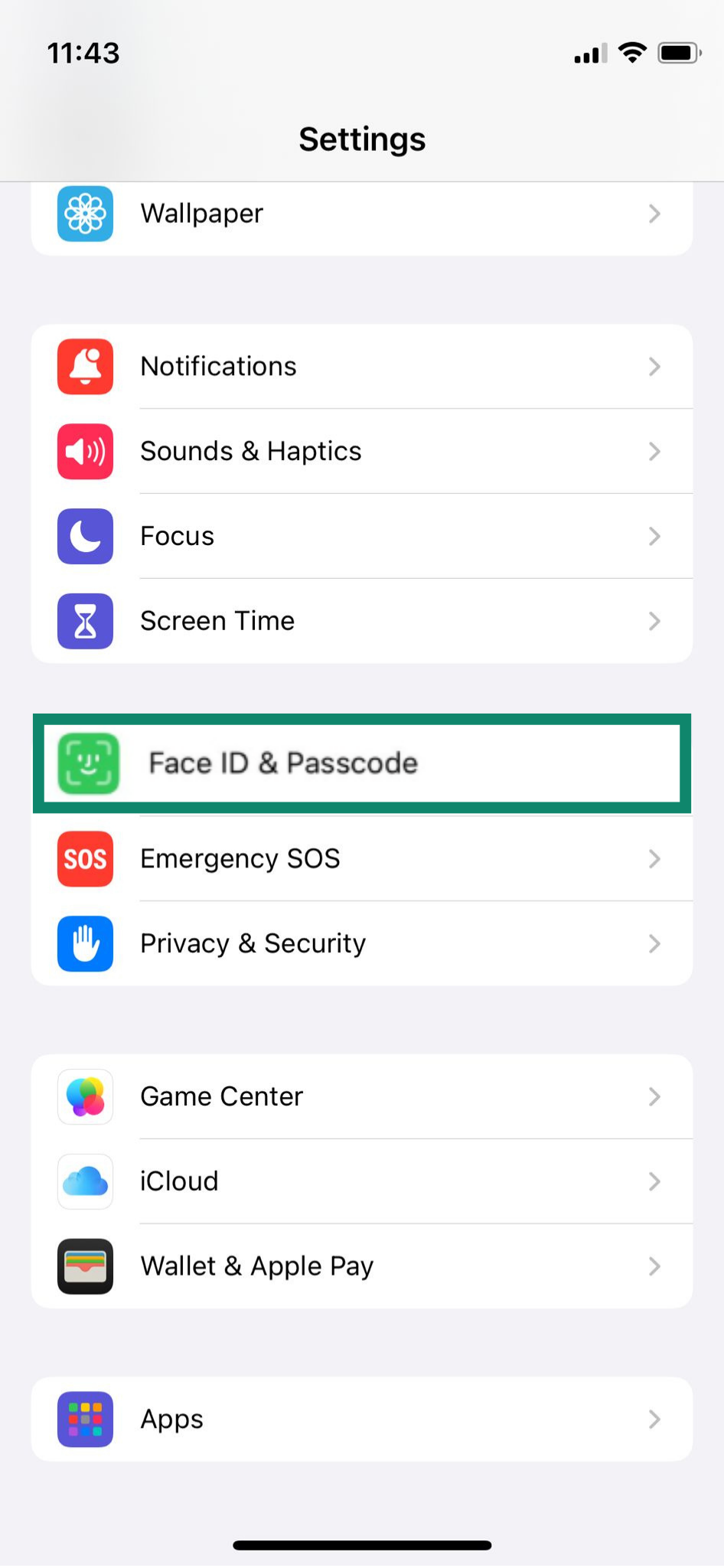
- Enter your passcode.
- Scroll to the section called Stolen Device Protection and make sure it’s turned on.
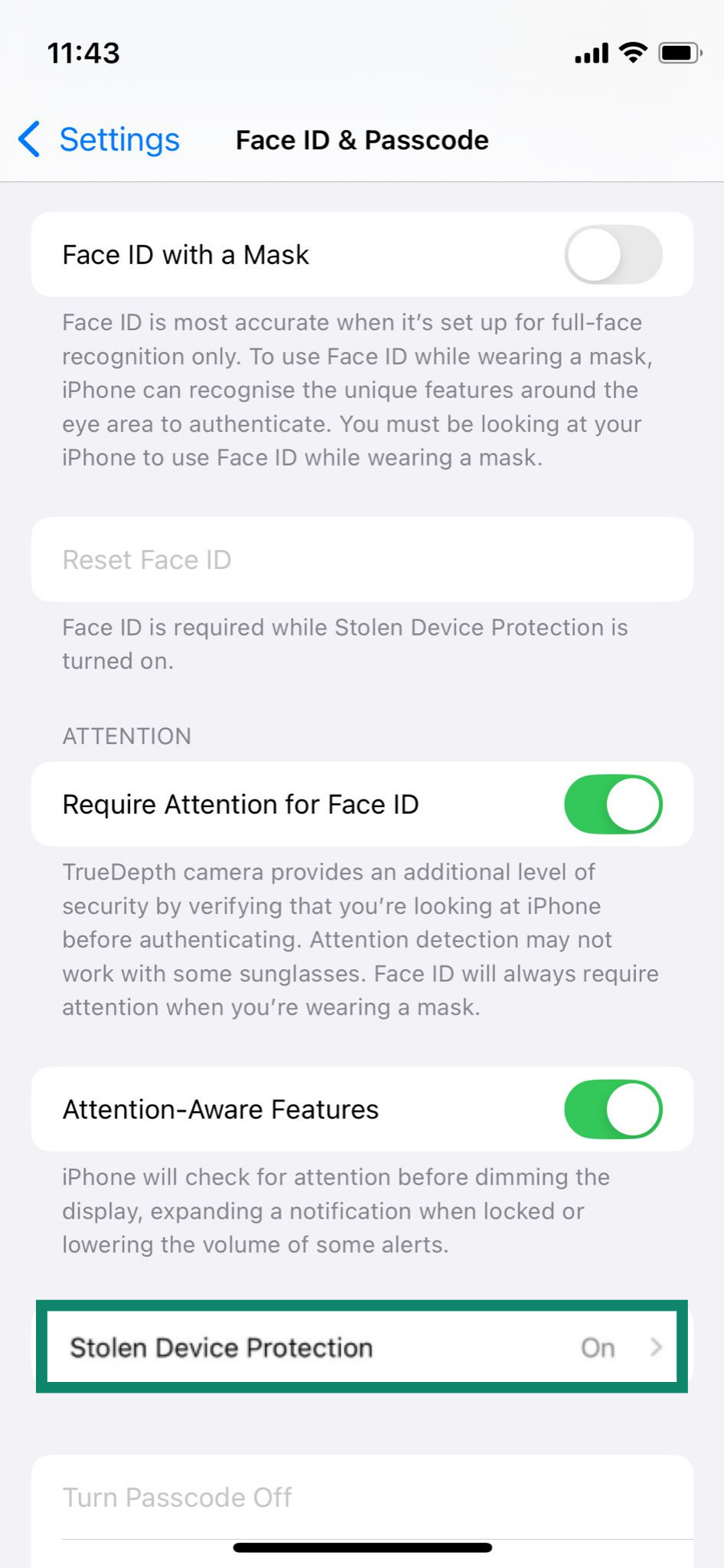
For extra peace of mind, iPhone users can enable Erase Data. This wipes the device after 10 failed passcode attempts. To turn it on, go to Settings > Face ID & Passcode, enter your passcode, then toggle on Erase Data.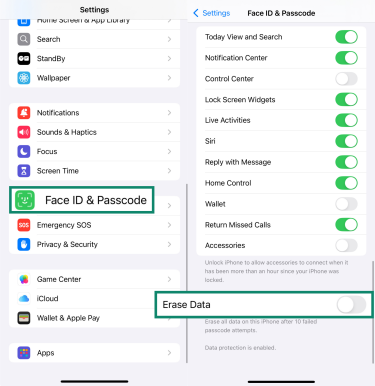
11. Back up data securely and regularly
Backups are your safety net against theft, resets, and ransomware. Enable encrypted cloud backups for photos, messages, and settings, and keep a local copy for extra safety. Test a restore so you know it works. Without a backup, wiped data is gone for good.
Remember that your phone’s security also depends on the account storing those backups. If someone gains access to your Apple or Google account, they can see your synced data. Protect it with a long, unique password and the strongest form of 2FA available.
Learn more: Read our detailed guide on how to back up files and encrypt them.
12. Avoid rooting or jailbreaking your device
Rooting (on Android) or jailbreaking (on iOS) means removing the built-in software limitations set by the manufacturer. While this allows for more customization, it does so by disabling the core security protections of the operating system, such as app sandboxing.
This makes your device far more vulnerable to malware and to privilege escalation attacks, where a malicious app can gain full administrative control over your phone.
Phone security for Android vs. iPhone
Android and iPhone both have strong security, but they approach it differently. iPhones focus on tight control and consistent updates, while Android offers more choice and flexibility. The result: both are secure, but how you set them up will vary.
Key differences in built-in security
Both platforms ship with strong defenses. The details differ, so your setup will differ too:
| iOS | Android | |
| App stores and reviews | iOS uses a “walled garden” approach with a single, strictly controlled App Store. Apple reviews every app before you can download it, creating a highly consistent security baseline. | Android’s model is more open. While the Google Play Store is the primary source for apps, Android allows you to install software from third-party stores or download it directly (“sideloading”), which adds choice but also risk. Google recently confirmed sideloading isn’t going away, though new rules will tighten how it works. |
| Permissions | Apps must explicitly request your permission via a system-level pop-up to access sensitive data (e.g., microphone, photos, location). Permissions are denied by default and can be granted on a temporary, one-time basis. | While modern versions require runtime permission requests, many core functions are tied to app suites (e.g., Google's) that have broad access by default. The granularity of control is generally less stringent than on iOS. |
| Sandboxes and system design | Every modern iPhone contains a Secure Enclave, a dedicated and isolated coprocessor that handles sensitive data like Face ID/Touch ID biometrics and encryption keys. | Android devices use a Trusted Execution Environment (TEE) for similar functions, but the specific hardware and its level of security can vary significantly between different manufacturers and models. |
| Security updates | Apple pushes security updates directly and simultaneously to all supported iPhones as soon as they are ready. This ensures rapid protection against newly discovered vulnerabilities. | Updates must be modified by each device manufacturer and sometimes approved by mobile carriers. This process often causes significant delays, leaving devices vulnerable for extended periods. |
OS-specific best practices
Android-specific recommendations include:
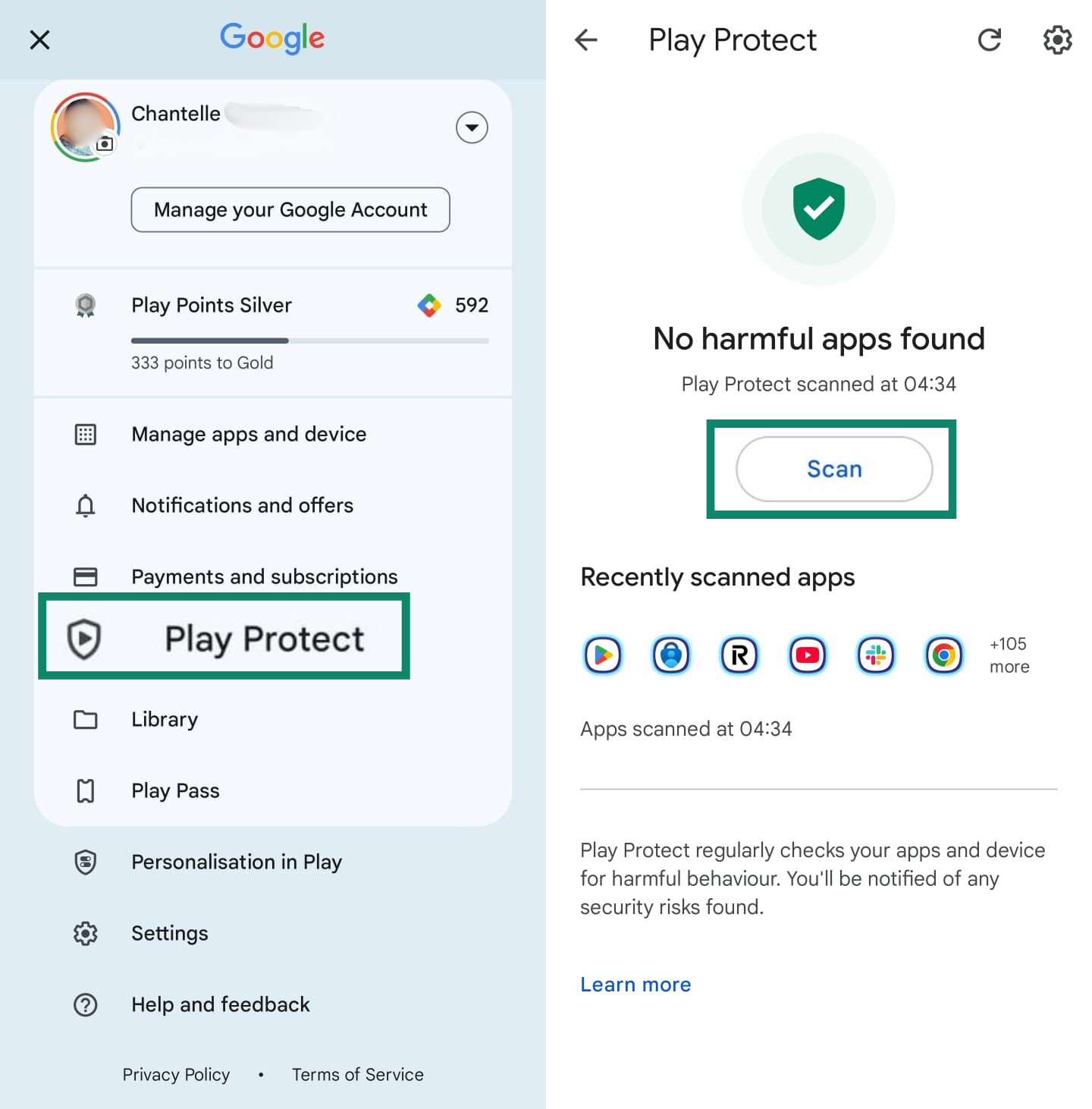
- Enable Google Play Protect and avoid third-party app stores. Open the Play Store, and tap the profile icon > Play Protect > Scan.
- Configure private Domain Name System (DNS) with trusted resolvers. This encrypts your DNS queries, preventing internet providers and network operators from seeing the websites you visit, adding a layer of privacy even when a VPN isn’t active.
iOS-specific recommendations include:
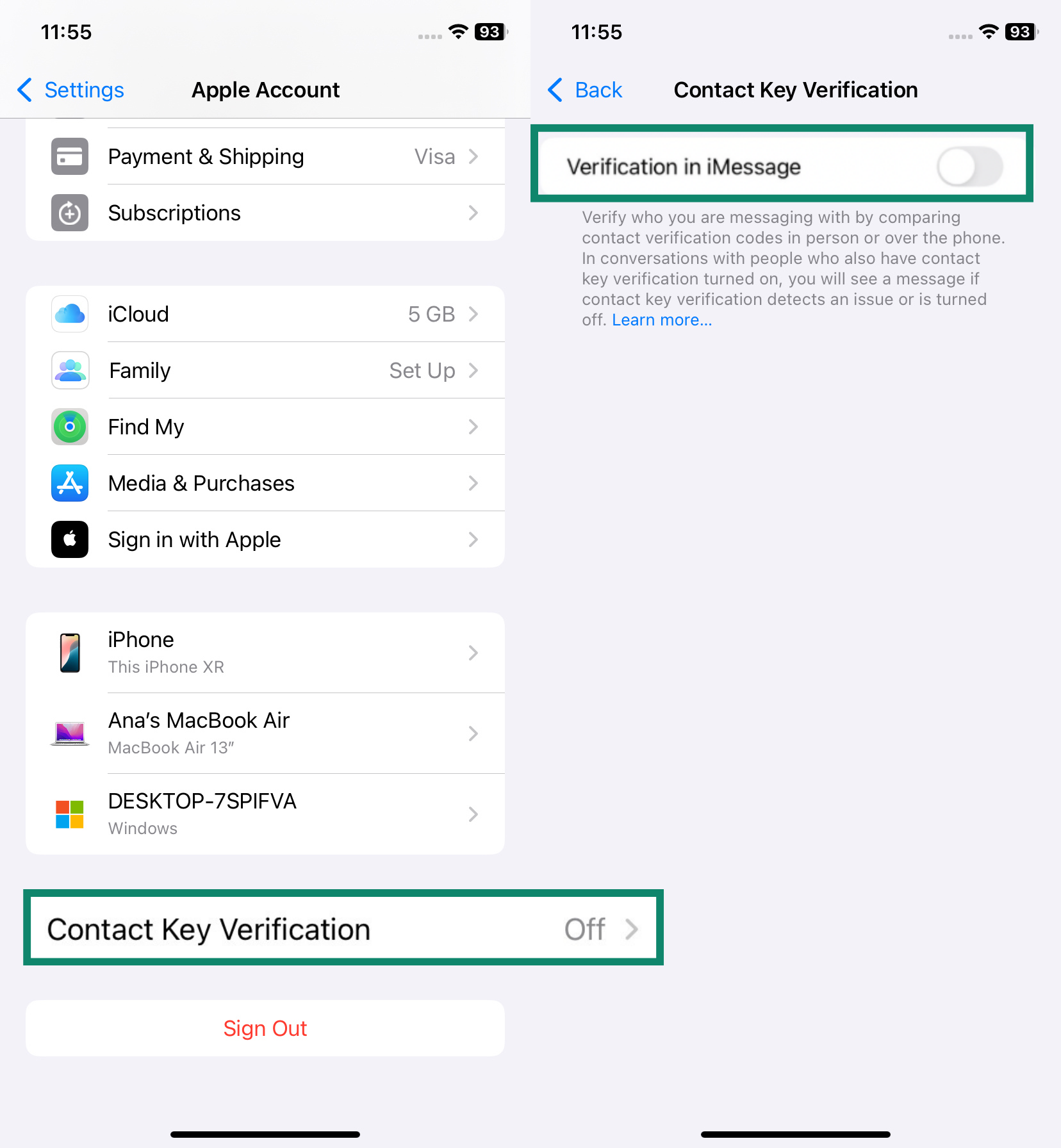
- Enable iMessage Contact Key Verification. This feature helps protect against highly targeted attacks designed to eavesdrop on your encrypted conversations. It lets you verify that you are messaging only the people you intend to and alerts you if an unrecognized device is ever added to your chat. Go to Settings > [Your Name] > Contact Key Verification. Toggle on Verification in iMessage.
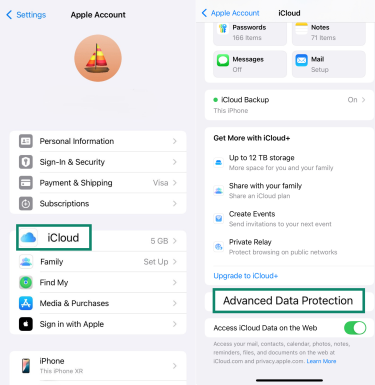
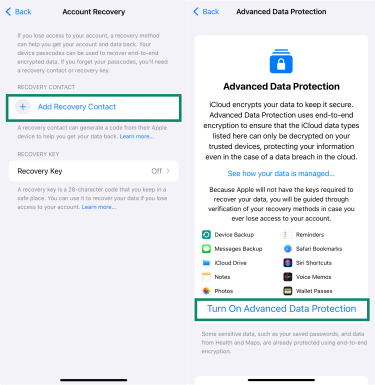
- Configure Advanced Data Protection for iCloud if available.
- Tap iCloud > Advanced Data Protection.
- Follow the prompts and add Recovery Contact. Click Turn On Advanced Data Protection.
- Tap iCloud > Advanced Data Protection.
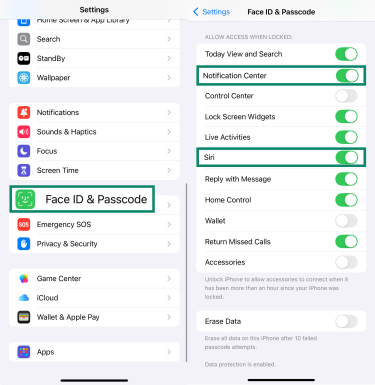
- Disable lock screen access to Control Center and Siri. Go to Settings > Face ID & Passcode. Scroll down to Allow Access When Locked, and turn off Siri and Notification Center.
- Use your phone's built-in privacy report to monitor how and when your apps access sensitive information.
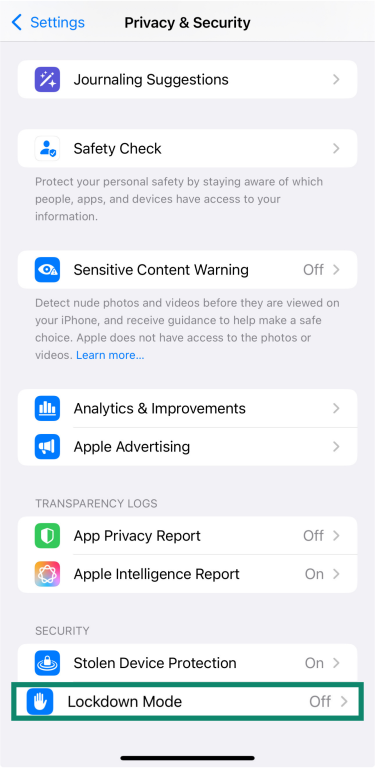
- Consider Lockdown Mode if your profession (e.g., journalist, activist) puts you at risk of targeted, zero-click exploits that bypass user interaction. This mode restricts certain apps and features to minimize attack surfaces, trading convenience for maximum security. Go to Settings > Privacy & Security > Lockdown Mode.
Signs your phone may be hacked
Your phone often provides clues when its security is compromised. Understanding these signs helps you respond quickly to protect your information.
Unexpected pop-ups or high data usage
Endless pop-ups, strange redirects, or new tabs may signal adware or spyware. Unusually high data use, especially at odd hours, can mean hidden apps are sending out information. Check per-app data use, or on iPhone use the App Privacy Report to spot suspicious activity.
Battery drains or performance lags
Malware running in the background can drain your battery and slow your phone. Check which apps use the most power; if an unknown one tops the list, delete it. On Android, scan with a trusted security app, and if issues continue, back up and reset.
Unauthorized app installs or messages
Finding apps you didn’t install, odd permissions, or messages you didn’t send usually means compromise. Remove suspicious apps, change your Apple or Google account password from another device, and secure your email and banking accounts first.
FAQ: Common questions about phone security
How do I secure my mobile phone?
The best approach is to layer protections. Keep your phone updated, install apps only from trusted sources, and limit unnecessary permissions. For safer browsing, use a VPN to encrypt traffic and reduce tracking, and consider an antivirus app for extra peace of mind.
What's the most secure way to lock your smartphone?
The strongest option is a long, unique passcode, which keeps your device encrypted and resists brute-force attacks. Avoid short PINs or swipe patterns, since they’re much easier to guess. On iPhone, you can also enable Lockdown Mode for extra protection if you’re at risk of targeted attacks.
Do I need antivirus on my phone?
Smartphones already come with strong built-in protections. Still, a trusted mobile antivirus can add an extra layer by spotting malicious apps, spyware, or phishing links that the default defenses might miss.
How can I tell if an app is spying on me?
It isn’t always obvious, but there are red flags. Watch for unexplained battery drain, overheating, or high data use: signs an app may be running in the background and sending data. Also be wary of apps asking for unnecessary permissions or showing strange pop-ups.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN