What is two-factor authentication (2FA), and how to set it up securely

These days, a password on its own may not offer enough protection for your accounts.
Passwords, along with other personal information, can sometimes be found for sale on the dark web. And weak or reused passwords are often easier for cybercriminals to guess or crack. To better protect your accounts, it’s a good idea to turn on two-factor authentication (2FA) wherever it’s available.
With 2FA turned on, you’ll need to provide a second form of verification on top of a password in order to access your account. This usually comes as a code sent via email, app, or text message, but other options include biometric authentication and hardware keys.
How two-factor authentication works
2FA works by securing your account with an extra level of protection. Instead of just needing one piece of information (like a password) to access an account, you’ll need two. Depending on the 2FA method being used, this second factor could be a code sent to your email, phone, or authenticator app; your fingerprint; or a piece of hardware.
Many 2FA methods rely on temporary one-time passwords (TOTPs) generated by an app. The website or service you're trying to access uses the same algorithm to independently generate the expected TOTP. Therefore, it’s able to check whether the TOTP you entered matches its own. A more basic and less secure method sees a site send you a randomly generated code via email or text. In either case, you entering the right code allows the service to verify that it's actually you trying to log in.
Authentication factors explained
Authentication factors fall into three categories: knowledge (something you know), possession (something you have), and inherence (something inherent to you). 2FA strengthens your account protection by requiring two factors from different categories.
Having 2FA ensures that even if a threat actor compromises one of these categories, you’re still protected from unauthorized access. Understanding the three types of authentication factors will help you identify the best ways to secure your account.
Knowledge factor (something you know)
Knowledge factors include things like passwords, PINs, and answers to security questions. These are widely used but highly vulnerable to phishing, brute-force attacks, and data breaches. A huge majority of websites, apps, and organizations use this type of factor to some degree.
To maximize the security of knowledge factors, make sure they aren’t easily guessable. When creating or changing a password, use random combinations of letters, numbers, and symbols. If you’re using a PIN, make it as long as possible. Avoid commonly used passwords, and consider using a password manager like ExpressVPN Keys to store, manage, and generate strong passwords.
Possession factor (something you have)
Possession factors rely on a physical item such as a smartphone or hardware security key. This helps prevent remote attacks because the attacker must also gain control of the physical item to log in. This factor of authentication is generally regarded as the most secure, but it can be inconvenient and lead to account lockout if you lose access to the physical authentication key.
Inherence factor (something you are)
Inherence factors are based on biological traits such as fingerprints, faces, voice patterns, or eyes. This kind of factor is convenient to use and hard to replicate, making it a popular choice for many people.
But unlike a password, biometric data can’t be changed. This can be a problem if, for example, someone is able to gather your fingerprint data and use it to create a passable 3D-printed copy. In that event, the cybercriminal could easily access any accounts that you can access with just a fingerprint.
For this reason, you should always couple an inherence factor with another form of authentication. It’s also worth noting that not every device supports biometric authentication.
Examples of 2FA in action
Depending on the factors you choose and the account you’re trying to access, the process of using 2FA can vary a bit. Here are a few examples of 2FA in action:
- Google: To access your Google account on a new device, you may need to tap a prompt sent to your phone.
- Microsoft: Microsoft pushes users to combine a password with the Microsoft Authenticator app, which generates temporary codes that serve as 2FA.
- GitHub: To log into GitHub, developers need both a password and a TOTP authenticator app or a security key (FIDO/U2F).
- Banking: Your bank may ask you to provide a code sent to you by SMS when logging in or after making a purchase online.
- Workplace logins: Many organizations require employees to use hardware tokens for 2FA when they need secure remote access.
Types of two-factor authentication
The most common types of 2FA are TOTPs sent via email, SMS, or authenticator apps. Other options include push-based notifications, hardware security keys, and biometrics (fingerprints, facial recognition, etc.). Each method has unique benefits and risks. 
SMS passcodes
SMS-based 2FA is the most widely used method, but it’s also rather vulnerable. It’s pretty simple: a code is sent to your phone via text, which you need to enter to log in. Typically, you need to enter the code after your password.
However, there are risks. Attackers are known to use SIM swapping to reroute texts to their own device. With the right timing, criminals could try to get you to hand over your code through a phishing link. Some skilled hackers can even exploit vulnerabilities in phone systems to directly intercept codes, though this is mostly used against high-profile targets.
That said, it’s a better option than only relying on passwords. Obtaining an SMS code requires great technical skill. Chances are, if someone is able to accomplish this, they could break into any account that’s only protected by a password. Still, organizations and privacy-focused users should consider using authenticator apps or hardware security keys instead.
Authenticator apps
Authenticator apps like Google Authenticator and Authy generate time-based TOTPs or QR codes that are only usable for a short period of time. They’re more secure than SMS because the codes are generated locally, meaning they can’t be intercepted on an unsafe network.
Push-based 2FA
Push-based 2FA lets you set up a trusted device that can be used to verify logins. When you attempt to log in, your trusted device will receive a prompt asking you to approve or deny a login attempt.
Clicking or tapping on a notification is faster than entering a code, but it’s vulnerable to push fatigue. Basically, some users are so used to these prompts, they click yes automatically, even if they’re not trying to log into an account. Some services protect against this by making it so users have to answer a more detailed prompt, but most do not. Despite this vulnerability, push-based 2FA is more secure than SMS or email-based methods.
Hardware security keys (U2F, FIDO)
Hardware-based 2FA methods like YubiKeys offer the highest level of protection. These keys are phishing-resistant and cannot be intercepted remotely. All you need to do is plug in the key to complete the authentication process. Of course, if you lose the key, you might be locked out of your accounts. For this reason, it’s advised to buy multiple keys and connect all of them to your accounts. Hardware keys are ideal for securing sensitive or high-value accounts.
Biometric authentication
Biometric 2FA uses unique physical traits such as a fingerprint or facial pattern as the second factor. It’s fast and convenient, but it isn’t perfect. Biometric data can’t be changed if it gets compromised, and spoofing attacks are possible on weaker systems. Not every device supports biometric logins, so this isn’t always an option.
How to set up two-factor authentication
Setting up 2FA varies depending on the app or website you're using, and some don’t even support 2FA. To enable 2FA, log into a website or app and look for the 2FA setting (it’s usually found under account or security settings). If you’re unable to find any 2FA options, contact customer support and ask if they offer 2FA.
Step-by-step setup via SMS
SMS-based 2FA is the simplest to set up and use. Here’s how you can enable SMS verification on just about any website or service.
- Go to the security settings of your account. Depending on the app, you may need to visit your password security settings or your account center.
- Select SMS/text message as your 2FA method.
- Enter your phone number.
- Confirm with the verification code sent via SMS.
- Save your changes.
Using authenticator apps
Authenticator apps are third-party apps that you link to your accounts. Using Google Authenticator as an example, here’s how to set one up.
- Install Google Authenticator from your phone's app store.
- Open the app and sign into your Google account.
- Next, log into the account, app, or service that you want to add 2FA to.
- Find the 2FA option; it’s typically within the privacy or security settings.
- Tap Authentication app or a similar option (the exact phrasing will vary).
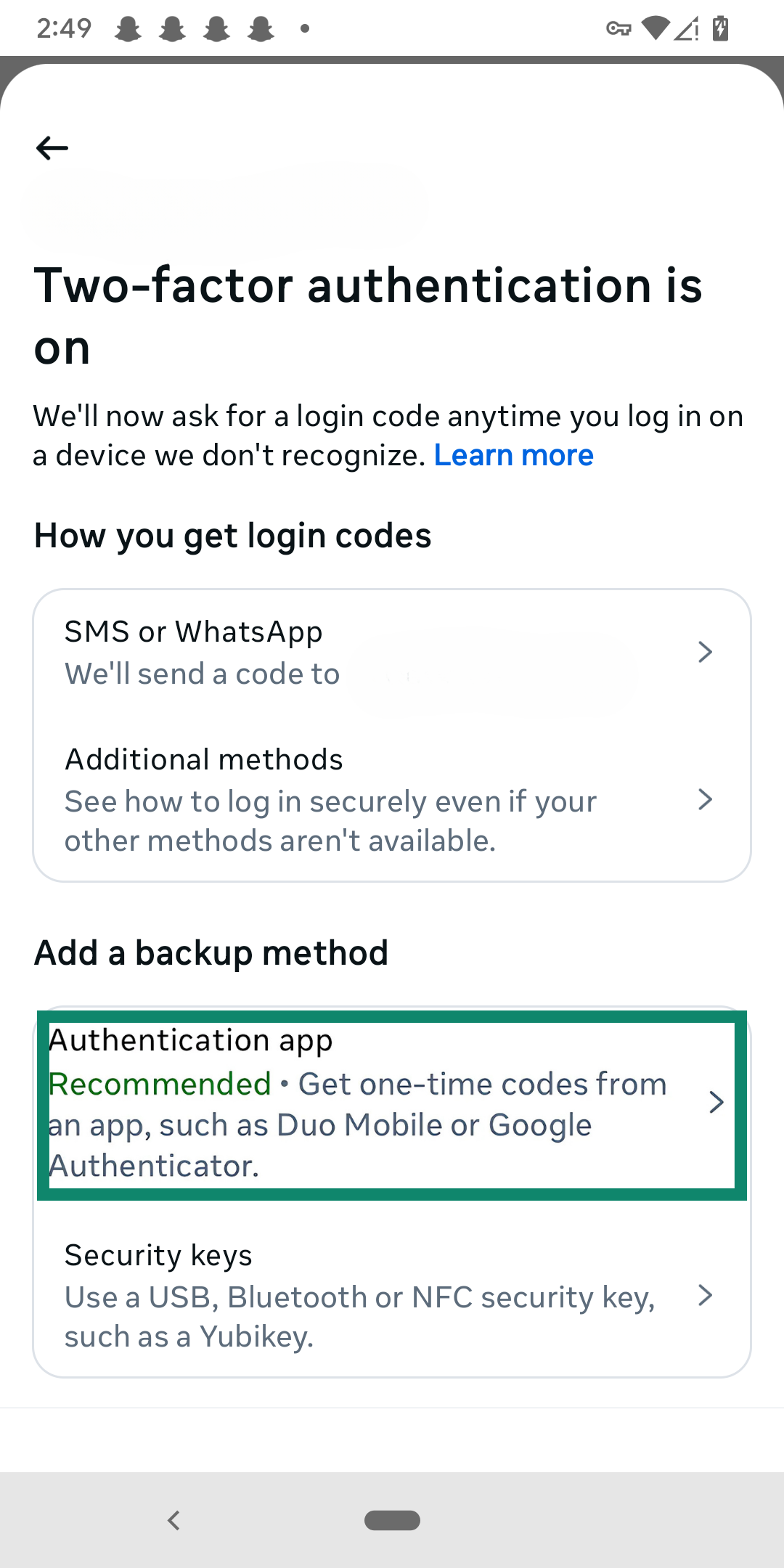
- You can either paste the provided code into Authenticator or scan the QR code provided.
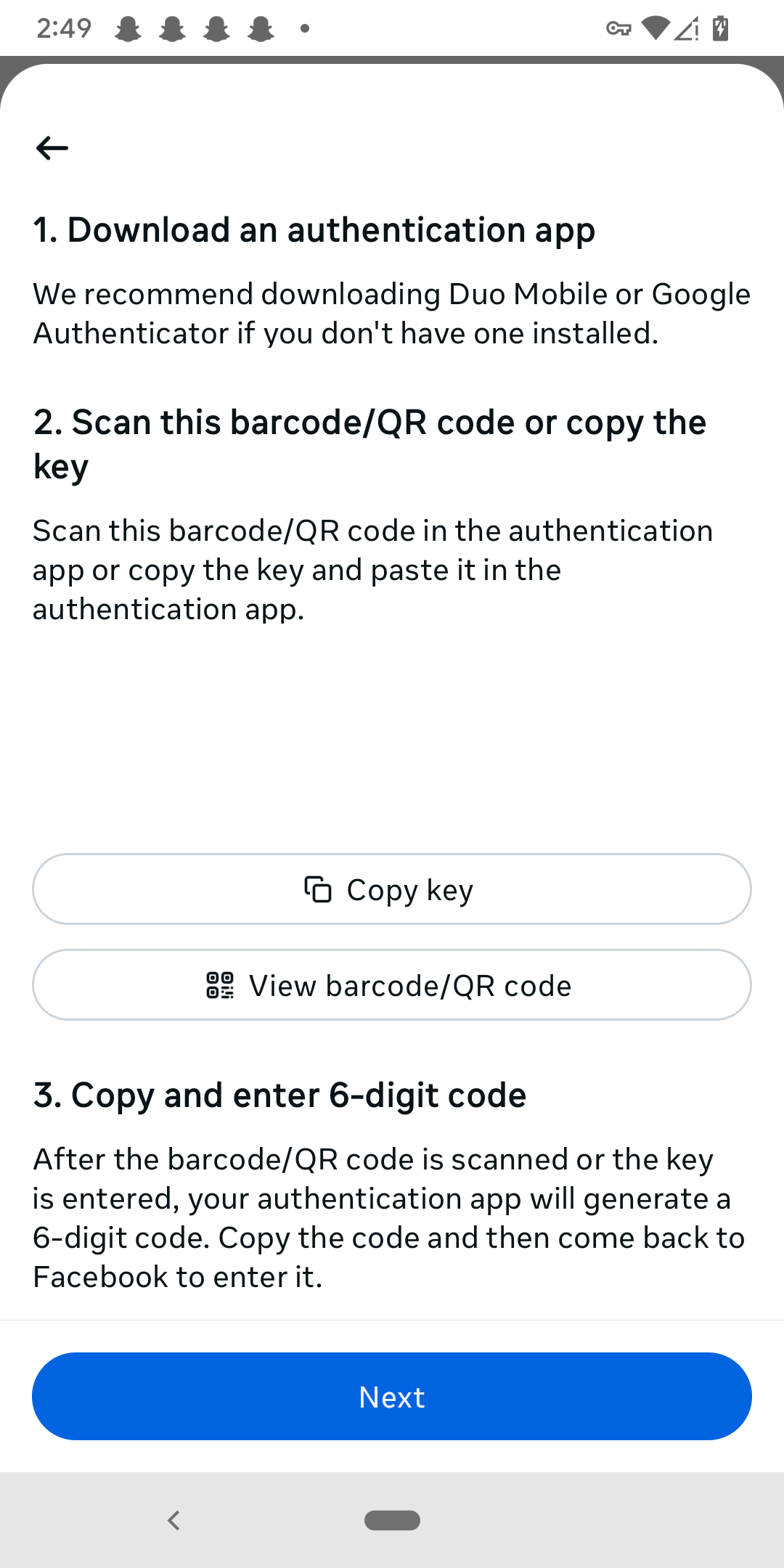
- Go back to the Google Authenticator app. Tap on the multicolored + sign in the bottom right corner.
- You can choose to either enter your generated code or scan the QR code.
- Save your backup codes.
That said, Google Authenticator collects more personal information than other authenticators, including your location, contacts, and device identifiers. That’s why you might want to consider using a password manager with an integrated authenticator.
Not every password manager has one, but ExpressVPN Keys and others allow you to generate 2FA keys for any password on your account (that supports app-based 2FA natively). Relatively few sites support authenticator apps, but for those that do, here’s how to set it up:
- Download an authenticator app.

- Open the website you want to add 2FA to and look for the service’s security settings. You can do this by tapping a saved entry and selecting EDIT.
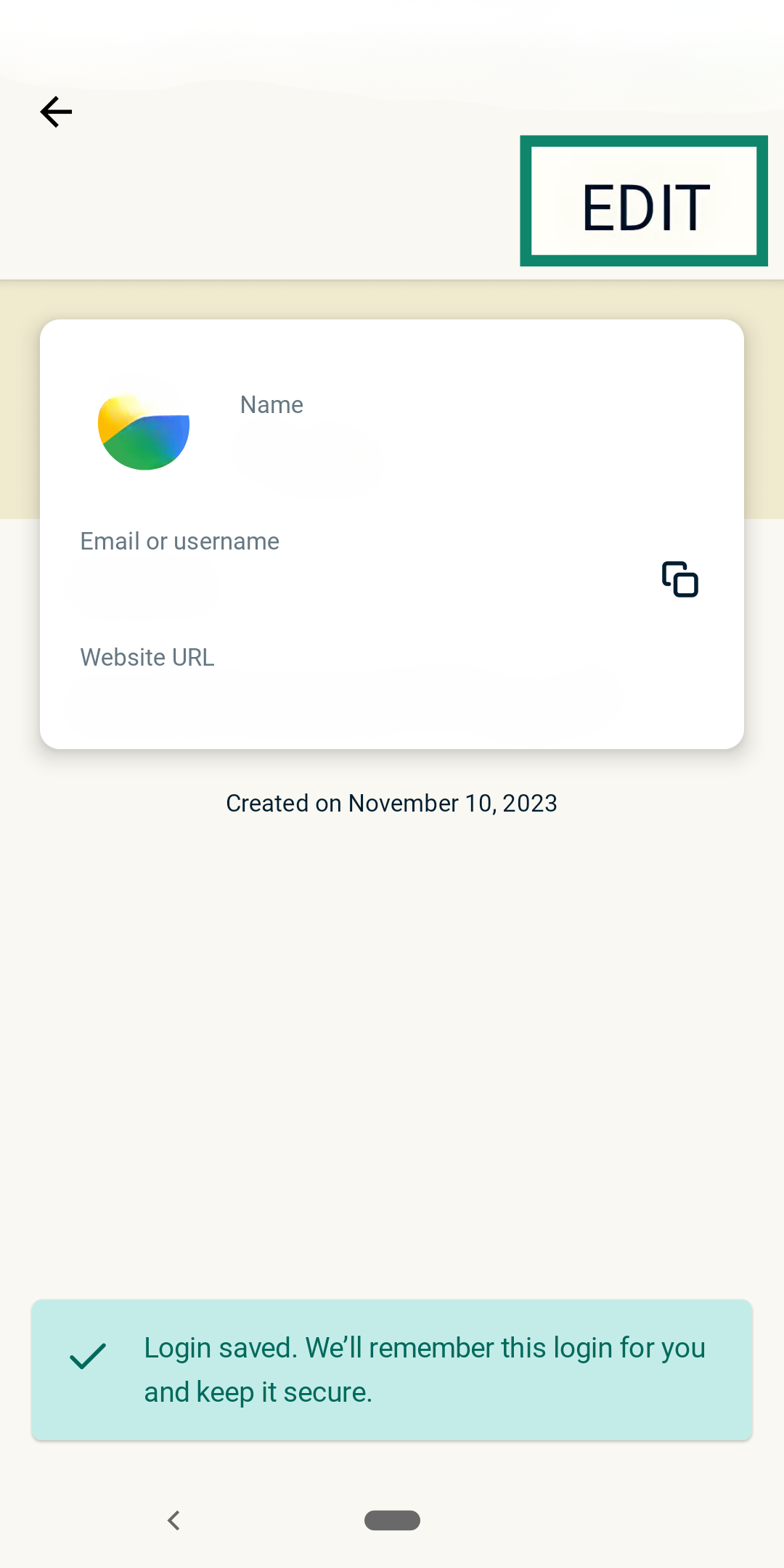
- Choose Set Up 2FA Verification Code.
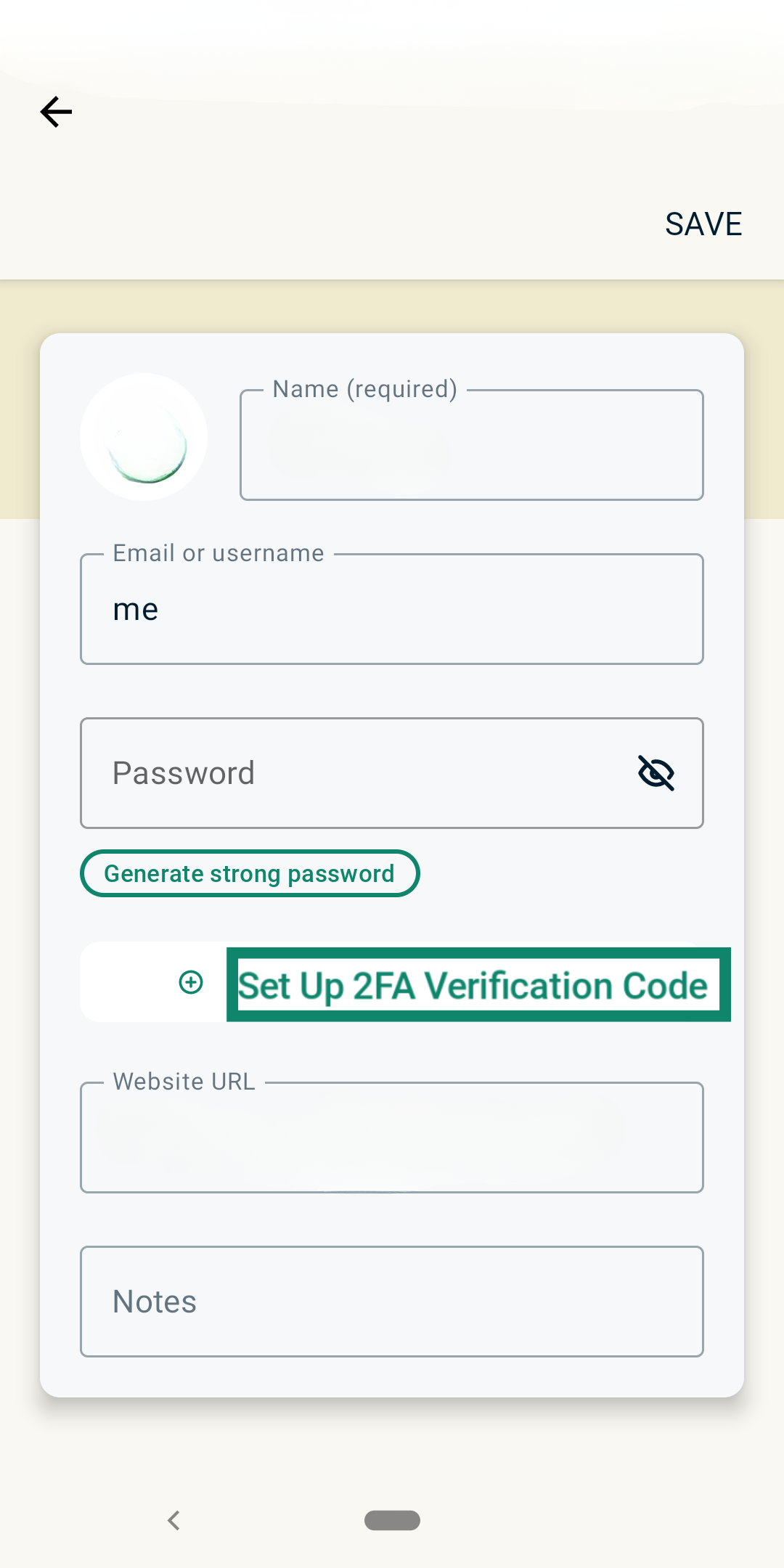
- Scan the QR code from the ExpressVPN app or enter the generated code to confirm. Depending on your authenticator app, this may happen before the QR code or in place of it.
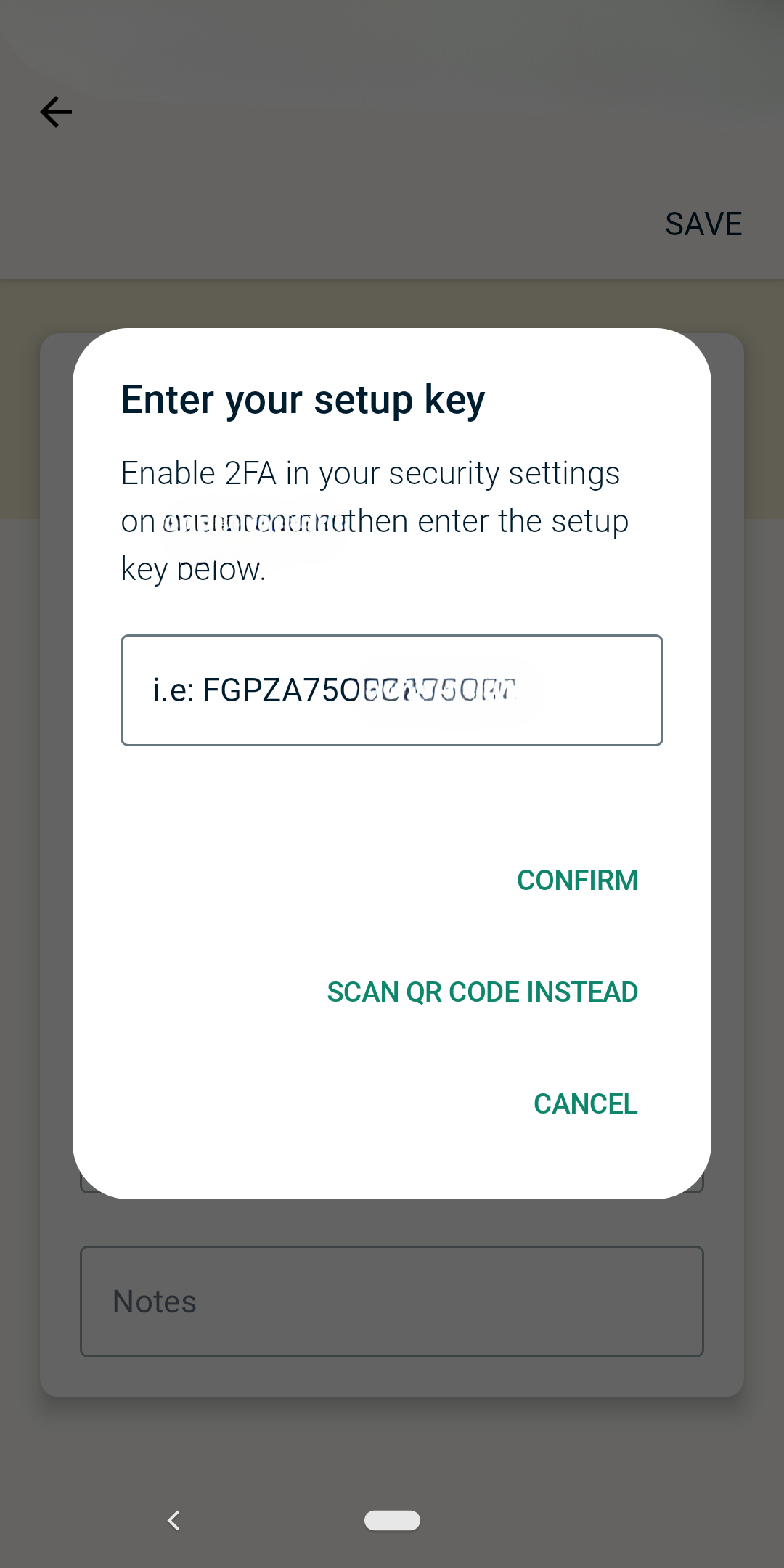
- Save your backup codes.
Setting up hardware tokens
Setting up a hardware key is more intensive than other solutions, particularly because you need to purchase a physical hardware key. While the process varies depending on which type of hardware key you get and the service you’re trying to pair it with, here’s a general guide to setting up a hardware token:
- Purchase a hardware key (ideally, get at least two).
- Plug in or pair the key(s) with your device.
- Go to your account’s 2FA settings.
- Select the hardware key as your method.
- Follow on-screen prompts to register the device.
- Confirm your choice.
Benefits and limitations of 2FA
2FA makes your accounts safer, full stop. It blocks most automated attacks and helps protect against phishing scams and other methods of gaining access to your accounts. That said, it doesn’t make you immune to being hacked, especially if you have poor password habits (reusing passwords, using very simple passwords, etc.).
Top security benefits of using 2FA
2FA improves your account security by requiring the use of a secondary form of verification to access an account. Even if a password is compromised, the attacker still needs the second factor, which is often time-sensitive or device-bound.
2FA is particularly important for organizations that manage sensitive data, access government systems, or are bound by data control regulations. Without 2FA, any criminal could acquire employee credentials and use them to spy on the organization or steal its data.
Average users benefit from 2FA, too. You may not have as much on the line as a large company, but you still have bank accounts, personal communication, and more to protect. Like companies, individuals are at risk of phishing scams, malicious websites, and automated attacks.
Can two-factor authentication be hacked?
Yes, 2FA can be hacked, though it’s far more difficult to compromise than a password by itself. Attackers can use phishing, man-in-the-middle (MITM), or other attacks to intercept or obtain your second factor.
SMS and email codes are most vulnerable. Codes sent over text are risky because of threats like SIM swapping, while email accounts are very common phishing targets due to the fact that they’re such a valuable target.
Hardware-based 2FA is more secure but less convenient for everyday use. For maximum security, we recommend installing phishing protections and using hardware security keys (FIDO2/U2F).
Known vulnerabilities and how to avoid them
Common 2FA vulnerabilities include phishing attacks, SIM swapping, and social engineering to reset authentication methods. SMS-based 2FA is particularly risky, as messages can be intercepted or rerouted. Email-based 2FA has a similar vulnerability, especially if the criminal gains access to your email account.
To avoid these threats, use app-based or hardware authenticators, enable biometric options if available, and never share codes with anyone. Consider using a password manager like ExpressVPN Keys to ensure that each of your passwords is strong, unique, and hard to crack. Organizations should monitor for suspicious account recovery attempts and train users to spot phishing attempts.
Multi-factor authentication (MFA) vs. two-factor authentication
MFA and 2FA both involve using more than one form of authentication to access an account. However, 2FA strictly refers to using exactly two factors, typically a password and a TOTP. MFA, on the other hand, means you’ll need two or more factors. Both offer extra layers of security and are more secure than simply using a password.
What’s the difference?
 The key difference is that 2FA is a subset of MFA. 2FA uses exactly two distinct authentication methods, like a password and a device-generated code.
The key difference is that 2FA is a subset of MFA. 2FA uses exactly two distinct authentication methods, like a password and a device-generated code.
MFA includes any combination of two or more factors, which could also involve biometrics, smart cards, location data, and authentication apps. MFA is broader and can provide stronger protection than 2FA, depending on how many and which factors are used. It’s more complicated, but that’s the cost of extra security.
When should you use MFA instead of 2FA?
Use MFA instead of 2FA when handling sensitive data, managing privileged access, or operating in high-risk environments. While 2FA helps prevent unauthorized access, the extra layers of security added by MFA make it even harder for attackers to bypass. For example, organizations protecting sensitive financial records or government systems benefit from MFA, since it makes it harder for someone to obtain employee credentials and use them to access confidential systems. In some cases, regulations may even require companies to use MFA.
In general, 2FA is effective in most cases, but MFA is ideal for organizations and highly sensitive accounts.
FAQ: Common questions about two-factor authentication
What does 2FA stand for?
2FA stands for two-factor authentication. It adds a second step to verifying your identity during logins, typically by requiring both a password and a second method, like a text code or biometrics. 2FA significantly reduces the risk of unauthorized access, even if someone has your password.
Is 2FA secure?
Yes, two-factor authentication (2FA) is secure. Without 2FA, anyone with your password can freely log into that app or account. With 2FA, they also need access to your secondary form of verification, which can include authentication apps or biometrics. However, it’s important to note that all forms of 2FA (email, text, app-based, and hardware) have their own unique risks. For example, email-based 2FA will be effectively useless if you use the same password on your email address as you do on the service that the criminal is trying to hack.
How do I know if a service supports 2FA?
There are two main ways to tell if a service supports two-factor authentication (2FA). Start by checking the website or app’s security settings for 2FA options. If you find any, all you need to do is enable them. If you don’t see any there, reach out to the company's customer support center and ask if 2FA exists.
What happens if I lose access to my second factor?
Losing your second factor can lock you out of your account. Most services offer backup codes or alternative methods to recover access, but this isn’t guaranteed. The U.S. National Institute of Standards and Technology (NIST) recommends setting up multiple authenticators at once so you can avoid being locked out and improve your security.
What is passwordless authentication?
Passwordless authentication replaces passwords with more secure methods, including biometrics, device-based logins, or hardware keys. It’s supported by modern security frameworks like FIDO2 and serves to minimize the risk of having your credentials stolen.
Which type of 2FA is the most secure?
Hardware security keys are considered the most secure two-factor authentication (2FA) method. They use cryptographic protocols and are phishing-resistant, unlike SMS-based codes. Whenever you log into a new account, you need the physical hardware, such as a USB stick or smart card, to authenticate your login. While secure, they’re also very inconvenient, which limits their popularity.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN

















Comments
Hallo and thanks
Hello and thank you for reading!
thanks
Thanks
must sefty account
Thanks
Thanks. A good app for generating 2FA codes is also from MS, Microsoft Autentificator. It has the option to backup all the codes.
Good
Where do I get the vpn Authenticator? My vpn is stopping my internet on laptop.
Here is more information on ExpressVPN's authentication: https://www.expressvpn.com/blog/expressvpn-app-authentication/ For issues with using ExpressVPN, please contact Support via live chat or email.