What is phishing-resistant MFA, and why does it matter?

Multi-factor authentication (MFA) is widely used to keep accounts secure. Traditional MFA methods include one-time passwords (OTPs) sent via email, SMS, or automated voice call, but these can be vulnerable to phishing attacks.
That's where phishing-resistant MFA comes in. Rather than using code that cybercriminals can intercept or steal via social engineering, it uses cryptographic verification that makes these attacks far more difficult to carry out.
In this guide, we’ll explain what makes an MFA method phishing-resistant, explore the most secure options available today, and look at the security gaps in older MFA approaches. We’ll also share how users can safely make the switch to phishing-resistant MFA.
Understanding phishing-resistant MFA
Phishing-resistant MFA uses cryptographic verification to combat phishing-related threats. To understand its significance, we first need to look at what phishing is and how it works.
What is phishing?
Phishing attacks trick users into sharing sensitive information by impersonating legitimate services. An attacker might send an email that looks like it's from your bank, complete with official logos and urgent language. When you click the link and enter your credentials into the fake site, you've handed them directly to the attacker.
According to the 2024 FBI Internet Crime Report, phishing is the most reported type of online crime by a significant margin, with over 190,000 complaints.
How phishing-resistant MFA differs from traditional MFA
Traditional MFA and two-factor authentication (2FA) add one or more extra verification factors, such as text message codes or authenticator apps, to the login process. This is more secure than just using a password, but the biggest weakness is that it doesn’t check where you're sending verification codes.
For example, say you receive a six-digit code via text, then type it into a login page. If that page is a phishing site, you've just given the attacker both your password and your verification code. They can immediately use these credentials to access your real account.
Phishing-resistant MFA mitigates this problem. A unique cryptographic key is generated between your device and the website or app. It’s stored on the device, and the website keeps a matching public key. Then, whenever you log in, the site sends a secure challenge that only your device can answer. It confirms that both sides are legitimate before any login information is shared.
What makes an MFA method phishing-resistant?
Phishing-resistant MFA uses a trusted device, such as your computer or phone, and cryptographic verification that is extremely difficult to fake or intercept.
From a user’s point of view, it’s simple. You might tap a security key, unlock your phone, or use your fingerprint or face scan to confirm it’s really you. Behind the scenes, your device and the service handle all the secure communication automatically.
This process is phishing-resistant because there’s no reusable code or credential for attackers to capture. Even if you visit a spoofed site, your device won’t complete the cryptographic challenge for an unrecognized domain, causing the authentication to fail before any data can be stolen.
Why traditional MFA solutions are failing
The Cybersecurity and Infrastructure Security Agency (CISA) states that while any MFA is better than no MFA, receiving a code via text, voice, or email is the least secure option.
Common vulnerabilities
SMS, email, and app-based authentication each have weaknesses that attackers can exploit. The table below shows the most common methods and which types of MFA they affect.
| Attack method | Applies to | Description |
| SIM swapping | SMS, voice | Attackers port your phone number to their device to intercept all verification codes. |
| Exploitation of the Signaling System 7 (SS7) protocol | SMS, voice | Criminals exploit weaknesses in the global signaling system to redirect messages and intercept authentication codes. |
| Phone number spoofing | SMS, voice | Attackers spoof your number or a trusted sender ID to impersonate you or deliver convincing phishing messages, tricking users into revealing OTPs. |
| Push fatigue (push bombing) | Push-based authenticator apps | Attackers send repeated login prompts until a user approves one out of frustration or habit. |
| Email account compromise | Attackers access your inbox to retrieve one-time codes or verification links. | |
| URL phishing | All methods | Fake or look-alike sites trick users into entering credentials and OTPs; attackers may use proxy pages to capture and relay codes in real time. |
Authenticator apps offer slightly better protection than SMS, but they’re not immune to phishing. As long as you’re manually entering a code, there’s potential for a fake login page to capture it.
Real-world phishing tactics that bypass MFA
Phishing goes far beyond easy-to-spot fake emails. Attackers now use a range of sophisticated tactics to trick users into approving access. These techniques can all succeed against traditional MFA methods.
Cybercriminals can create websites that convincingly mimic legitimate sites. These fake sites act as proxies, sitting between you and the legitimate service. When you enter your credentials and MFA code, the proxy forwards them to the real site and uses them to log in. Because this happens instantly, your code is still valid. You see what looks like a normal login page, but the attacker now has full access to your account.
Session hijacking takes this technique one step further. In an adversary-in-the-middle (AITM) scenario, once attackers use your credentials and MFA code to establish a session, they can capture the session cookies and stay logged in even after you sign out. More broadly, session hijacking can also occur when an attacker compromises a user’s device and steals authentication tokens directly, allowing them to carry that session over to a system they control. Either way, the attacker ends up with long-lasting access that MFA alone can’t prevent.
Social engineering compounds these technical vulnerabilities. Attackers craft urgent scenarios like security alerts or password expiration notices. Under pressure, users make mistakes and enter credentials into fraudulent sites.
User frustration with legacy methods
Beyond security concerns, traditional MFA has become frustrating for many users. Some common complaints include:
- Frequent prompts: Re-entering multiple authentication factors for routine logins quickly leads to fatigue and frustration.
- Complex setup: Managing different MFA apps and configurations across several accounts can be confusing and time-consuming.
- Unnecessary friction: Being asked for MFA in low-risk situations can feel excessive.
The danger is that when MFA feels inconvenient, users look for shortcuts or skip it altogether, weakening overall security.
Recovery processes add another challenge: if you lose your phone or can’t access your email to get the code, you’ll need to go through a time-consuming account recovery procedure.
Proven phishing-resistant MFA methods
There are several phishing-resistant authentication methods; each uses cryptographic verification to confirm your identity and the service's authenticity.
Fast Identity Online 2 (FIDO2) and Web Authentication (WebAuthn)
FIDO2 represents the gold standard for phishing-resistant authentication. This open standard uses public-key cryptography to verify both the user and the service. The FIDO Alliance developed these specifications specifically to eliminate phishing vulnerabilities.
WebAuthn serves as the web component of FIDO2. When you register with a website using WebAuthn, your device generates a unique cryptographic key pair. The private key never leaves your device, while the public key goes to the server.
During authentication, the server sends a challenge that only your device's private key can solve. This happens automatically through your browser. An attacker's fake site can't forge this challenge because it doesn't have the proper cryptographic relationship with your device.
Biometric authentication
Your fingerprint, face, and even how you type can serve as a phishing-resistant factor when properly implemented. Modern biometric systems store your biometric data locally on your device, never sending it to servers or across networks.
When combined with FIDO2, biometrics verify your identity to unlock the cryptographic key on your device. You scan your face or fingerprint, which proves you're the authorized user, and your device then completes the cryptographic authentication with the server.
It’s worth noting that biometrics used alone are generally considered a convenience feature rather than a strong security control; what makes them secure in this context is how they’re paired with cryptographic authentication.
Security keys (e.g., YubiKey, Titan Key)
Physical security keys, which connect via USB or near-field communication (NFC), provide excellent protection against phishing attacks. The attacker would need to steal the actual key to access your account, and even then, they may need your biometrics to access the data.
YubiKey leads the security key market with devices supporting multiple authentication protocols. The keys work with FIDO2 and also support older standards for compatibility with legacy systems. You simply insert the key and touch it when prompted. Google's Titan Security Keys offer similar functionality. Many models also support NFC or low-power Bluetooth, making mobile authentication even more convenient.
Smart cards
Smart cards are embedded with chips that store cryptographic certificates. For the card to work, you typically need both the physical card and a PIN.
The downside is that smart cards require additional infrastructure. Organizations need card readers connected to their computers, card management systems to issue and track cards, and processes to handle lost or damaged cards. This overhead makes them less practical for consumer applications, but they’re valuable for enterprises with existing infrastructure.
Comparing MFA options
Multi-factor terminology can be confusing and ambiguous; let's clarify the distinctions that matter for security.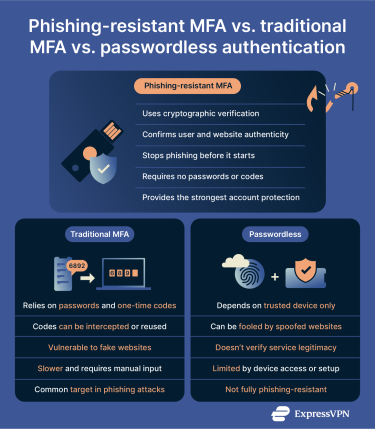
Phishing-resistant MFA vs. 2FA
2FA simply means the addition of a second requirement, in addition to a password, when logging in. This second factor can use the phishing-resistant methods discussed earlier, such as biometrics, a FIDO2 security key, or a smart card.
However, many 2FA setups use traditional methods that are susceptible to phishing attacks. Typical examples include receiving a code by text message, email, or an authenticator app. Fake login pages and social engineering can intercept, relay, or trick users into providing these factors.
When evaluating authentication methods, ask yourself whether an attacker with a convincing fake website could steal your credentials. If the answer is yes, the method isn't phishing-resistant, regardless of how many factors it uses.
Passwordless MFA vs. phishing-resistant MFA
Passwordless authentication uses various methods, such as biometrics, security keys, social logins, and magic links sent to your email, to access an account. This is an improvement on traditional passwords in some ways: the risk of passwords is that if one password is leaked in a data breach, it can impact other accounts where the same password is used, especially if you don’t use a strong, unique password for every account.
However, not all passwordless methods are phishing-resistant. Magic links sent via email can be intercepted. Some passwordless systems use SMS codes as the sole authentication factor, which remains vulnerable to SIM swapping and other interception. Even social logins can be targeted if they rely on credentials rather than cryptography.
Using FIDO2-based passwordless authentication is the best security practice, as it offers the advantages of both methods. You authenticate using a biometric or PIN on your device, which unlocks a cryptographic key that verifies your identity to the server. No password exists to steal, and the cryptographic verification prevents phishing.
How to implement phishing-resistant MFA (for organizations)
Implementing a phishing-resistant MFA system within organizations requires careful planning and execution; a poorly planned rollout can create security gaps and user frustration.
Key steps for successful deployment
- Audit your current authentication systems: Find out which applications your users access, what authentication methods they currently use, and where vulnerabilities exist. This allows you to prioritize and helps you phase implementation strategically.
- Choose your authentication technology based on your environment: Organizations with existing device management might deploy FIDO2 through Windows Hello or Apple's Face ID. Companies needing hardware tokens should evaluate security key options from providers like YubiKey or Google.
- Run a small-scale rollout to gather feedback: Start with a small group of users to test your authentication platform. They can flag any issues before your large-scale rollout.
- Plan your registration process carefully: Users need to enroll their authentication methods, which requires access to both their existing credentials and their new phishing-resistant factor. Schedule enrollment during work hours with IT support available.
- Build contingencies for device loss or failure: Assume some users will lose security keys or break phones with biometric sensors. Establish clear procedures for temporary access and re-enrollment that maintain security while minimizing disruption.
Tailoring solutions to your infrastructure
There’s no one-size-fits-all solution for creating and implementing a phishing-resistant MFA. There are various factors to consider, including the current infrastructure, how your systems run, and whether you’re dealing with in-house personnel, remote workers, or contractors.
- Cloud-first organizations have the easiest path to phishing-resistant MFA: Major providers like Microsoft Azure AD, Okta, and Google Workspace have integrated FIDO2 support. You can enable these features through admin settings.
- On-premises systems require more planning: You might need to upgrade identity management infrastructure or deploy additional components. Some legacy applications lack support for modern authentication protocols entirely.
- Hybrid environments are complex: Authentication needs to work consistently whether users access cloud services or on-premises resources. Consider identity federation solutions that provide unified authentication across both environments.
- Remote workers need special consideration: Remote work introduces new security and usability challenges that traditional identity and access management (IAM) systems weren’t designed to handle. Employees are often juggling multiple credentials across home networks and unmanaged devices.
Training and onboarding end users
Many people are resistant to change. If they logged into a site with just a password and never had a problem, it can be difficult to explain why the change is necessary. Therefore, you need a comprehensive plan for these users.
- Clear communication prevents confusion: Explain why you're implementing phishing-resistant MFA in terms that your users can understand. Focus on the benefits: better security, protection from phishing, and ultimately a smoother authentication experience.
- Provide hands-on training before the deadline: Walk users through the enrollment process step-by-step. Show them what to do when logging in with their new authentication method, and record these sessions for people who miss the training.
- Create easy-to-follow documentation: Include screenshots for each step. Address common questions like what happens if they forget their device, how to use their security key on different computers, and who to contact for help.
- Make support accessible during rollout: Staff your helpdesk with people trained on the new system, and consider extending support hours during the initial deployment phase.
Common pitfalls and how to avoid them
Here are some common mistakes to avoid for a smooth rollout.
- Rushing deployment: If you move too quickly, users may feel overwhelmed, mistakes might multiply, and adoption can suffer. Build a realistic timeline that accounts for training, testing, and a gradual rollout.
- Ignoring legacy systems: Some applications might not support your authentication protocols. Identify these early and plan alternatives like restricted access or updating the application.
- Overlooking account recovery: Some users will need to recover access after losing their authentication factor. Be proactive and develop a solution ahead of time instead of trying to figure it out when it happens.
- Forgetting shared accounts: Service accounts, shared administrative credentials, and emergency access accounts need special handling. Consider password managers with MFA or privileged access management solutions.
How phishing-resistant MFA strengthens VPN and remote access
Phishing-resistant MFA protects corporate virtual private networks (VPNs) and other remote access tools by confirming each user’s identity before a connection begins. It ensures that only verified users can reach corporate systems, even from outside the network perimeter.
MFA for VPN access control
Remote access and site-to-site VPNs create encrypted tunnels that secure data traveling between a user’s device and the company network. But before that tunnel is established, users still need to authenticate. If this step relies only on a standard username-and-password combination, the VPN login becomes vulnerable to phishing; if an attacker manages to steal these credentials, they can attempt to access the network just like a legitimate user.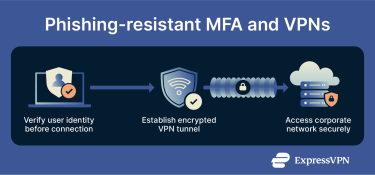
Adding a phishing-resistant MFA method to the VPN login process helps close this gap. Now, even if a user’s VPN password is compromised, it can’t be used on its own, as the login still requires the cryptographic key stored on the user’s device.
Many enterprise VPNs seamlessly integrate with FIDO2 authentication. Users authenticate using their security key or biometric before the VPN connection is established, ensuring that only authorized users with physical possession of authentication devices can access network resources.
Integration with zero-trust architecture
Zero-trust architecture is based on the assumption that nothing is trusted by default. Users don’t just authenticate once at login; the system evaluates each access request and may require reauthentication based on risk, device posture, or session context.
Phishing-resistant MFA enables zero-trust authentication by using cryptographic credentials that can’t be intercepted or reused, allowing secure reauthentication without disrupting the user experience.
Enhancing security for remote and hybrid workforces
The shift to remote work increased phishing attacks targeting corporate credentials; attackers know that remote workers access sensitive systems in less secure environments. Phishing-resistant MFA significantly mitigates the risk of credential theft via phishing by providing consistent security regardless of location.
Whether users connect from the office, home, or the public Wi-Fi network at a coffee shop, cryptographic authentication prevents malicious actors from accessing the corporate server. This simplifies security management while also improving protection.
Hybrid work environments also benefit from phishing-resistant approaches, especially with a bring-your-own-device (BYOD) policy, because phishing-resistant MFA works across managed and unmanaged devices.
Business benefits of phishing-resistant MFA
Reduced risk and compliance support
A single breach can cost millions in data loss, downtime, and reputational damage. According to IBM’s Cost of a Data Breach Report, the average incident reached $4.4 million in 2024. However, the financial impact is only part of the story. Breaches may also lead to regulatory penalties, litigation, and mandatory disclosure requirements under laws such as the General Data Protection Regulation (GDPR).
Phishing-resistant MFA helps reduce these risks by preventing attackers from stealing credentials and gaining unauthorized access in the first place. By ensuring authentication is cryptographically bound to both the user and the service, it closes one of the most common entry points for breaches.
When combined with encrypted network connections and secure access controls, phishing-resistant MFA strengthens defenses, lowers breach exposure, and helps organizations meet evolving legal and regulatory obligations.
Improved user experience
Better security doesn’t have to create friction. Modern phishing-resistant methods often make sign-ins faster and easier than traditional MFA. Biometric authentication with tools like Windows Hello or Face ID lets users glance at their device or simply touch a sensor to unlock a cryptographic key. By contrast, SMS codes and authenticator apps add extra steps and potential errors.
Security keys also bring consistency across devices. A single YubiKey or similar token works with laptops, phones, and tablets without configuration changes.
Passwordless implementations go even further. With no passwords to remember or reset, users save time and avoid weak credentials altogether.
Long-term cost efficiency
Implementing phishing-resistant MFA can require an upfront investment for hardware tokens, setup time, and potential infrastructure updates. But the long-term gains outweigh these costs. By mitigating risk, organizations avoid the expenses that come with incident response and recovery.
Many organizations spend heavily on support for locked accounts and forgotten passwords. Passwordless authentication removes most of that burden (although support is still occasionally needed for lost tokens or devices). What’s more, some cyber-insurance providers may offer lower premiums to companies that adopt phishing-resistant MFA.
FAQ: Common questions about phishing-resistant MFA
Is Microsoft Authenticator phishing-resistant?
While Microsoft Authenticator supports multi-factor authentication (MFA), it’s not phishing-resistant. Attackers can use phishing techniques to get users to give them the one-time password (OTP). For phishing-resistant protection, Microsoft recommends enabling Fast Identity Online 2 (FIDO2)-based authentication, like Windows Hello or security keys, to avoid phishing attacks.
Does multi-factor authentication (MFA) protect against phishing emails?
It depends on the type of MFA used. Traditional MFA, such as SMS, email, or app-based codes, can be vulnerable because attackers can trick users into entering their password and code on a fake site. Phishing-resistant MFA, on the other hand, prevents this by using cryptographic verification between the user’s device and the legitimate service, so even if a user clicks a phishing link, the authentication request will fail.
How much does it cost to implement a phishing-resistant multi-factor authentication (MFA)?
Costs vary based on your organization’s size and infrastructure. Many modern systems already support phishing-resistant authentication, like Fast Identity Online 2 (FIDO2), Web Authentication (WebAuthn), and platform biometrics, without extra licensing fees. The main expenses include hardware security keys, IT setup time, and training, although further costs can arise from compatibility issues, integrating legacy applications, and managing lost or replaced keys.
Are there industries where phishing-resistant multi-factor authentication (MFA) is especially important?
Any industry that handles sensitive or regulated data will benefit from phishing-resistant MFA. It’s especially critical in finance, healthcare, government, and defense, where compliance frameworks require strong authentication.
What standards support phishing-resistant multi-factor authentication (MFA)?
Fast Identity Online 2 (FIDO2) and Web Authentication (WebAuthn) are the core standards for phishing-resistant MFA. FIDO2 is the technical foundation, and WebAuthn is the web component. Together, they allow browsers and devices to perform cryptographic authentication.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN